ida32打开
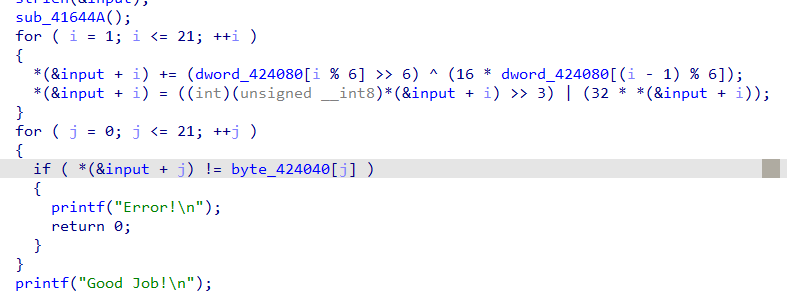
稍微调试了一下
发现是逐个字符加密然后逐个字符校验,直接上angr
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| import angr
from angr import *
proj = angr.Project("./attachment.exe", auto_load_libs=False)
stat_adr = 0x004164F8
user_input = 0x00426020
state = proj.factory.blank_state(addr=stat_adr)
simfd = state.posix.get_fd(0)
data, real_size = simfd.read_data(22)
state.memory.store(0x00426020, data)
simg = proj.factory.simulation_manager(state)
simg.one_active.options.add(options.LAZY_SOLVES)
false_path = 0x004164EA
flag_path = 0x00416609
simg.explore(find=flag_path, avoid=false_path)
if simg.found:
ans = simg.found[0]
sol = ans.posix.dumps(0)
print(sol.decode("utf-8"))
|
npuctf{WDNMD_LJ_OBFU!}

