第三届陕西省赛Rewp
第三届陕西省赛 Reverse WP
ezupx
估计抹掉了upx头,手脱
看到upx的标志,两个call ebp,加上里面还是VirtualProtect
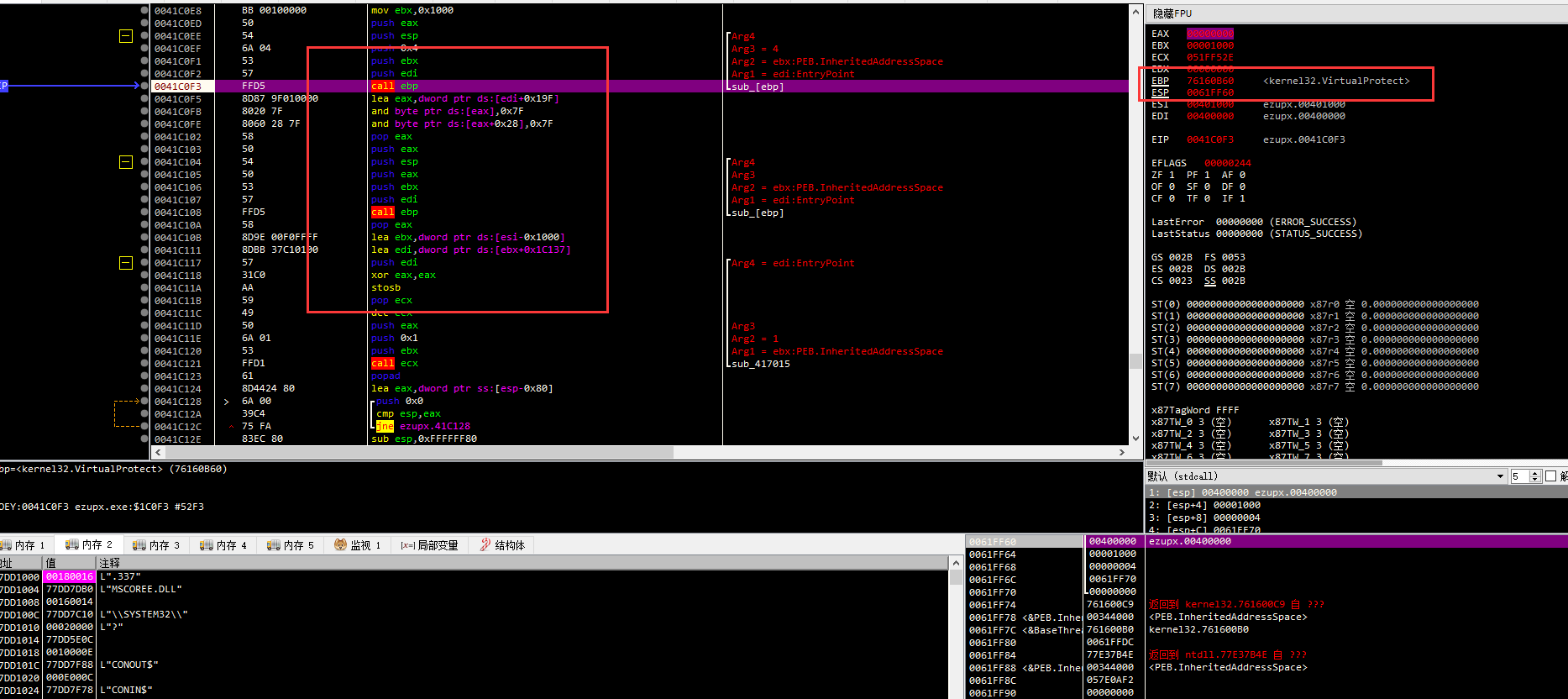
那么后面的那个jump估计就是了,dump出来静态分析
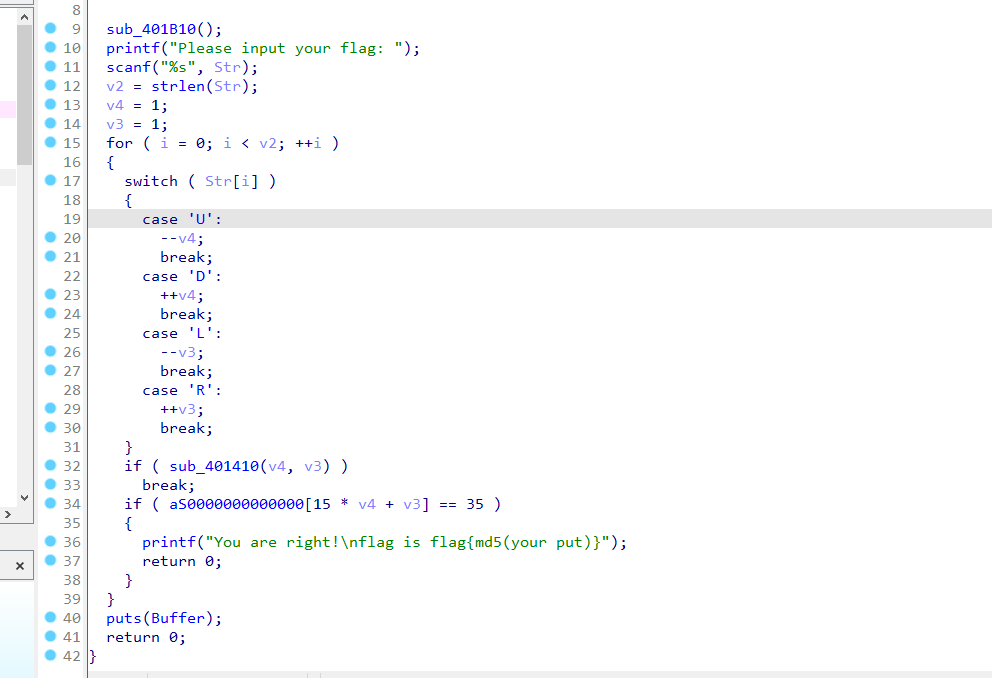
迷宫题,迷宫长这样
1 | *************** |
找到最短路径:RRRDRRURRRRRRDDDDRDDD
1 | flag{ae2de0be8285f69db701d4dba8721a40} |
babypy
py字节码
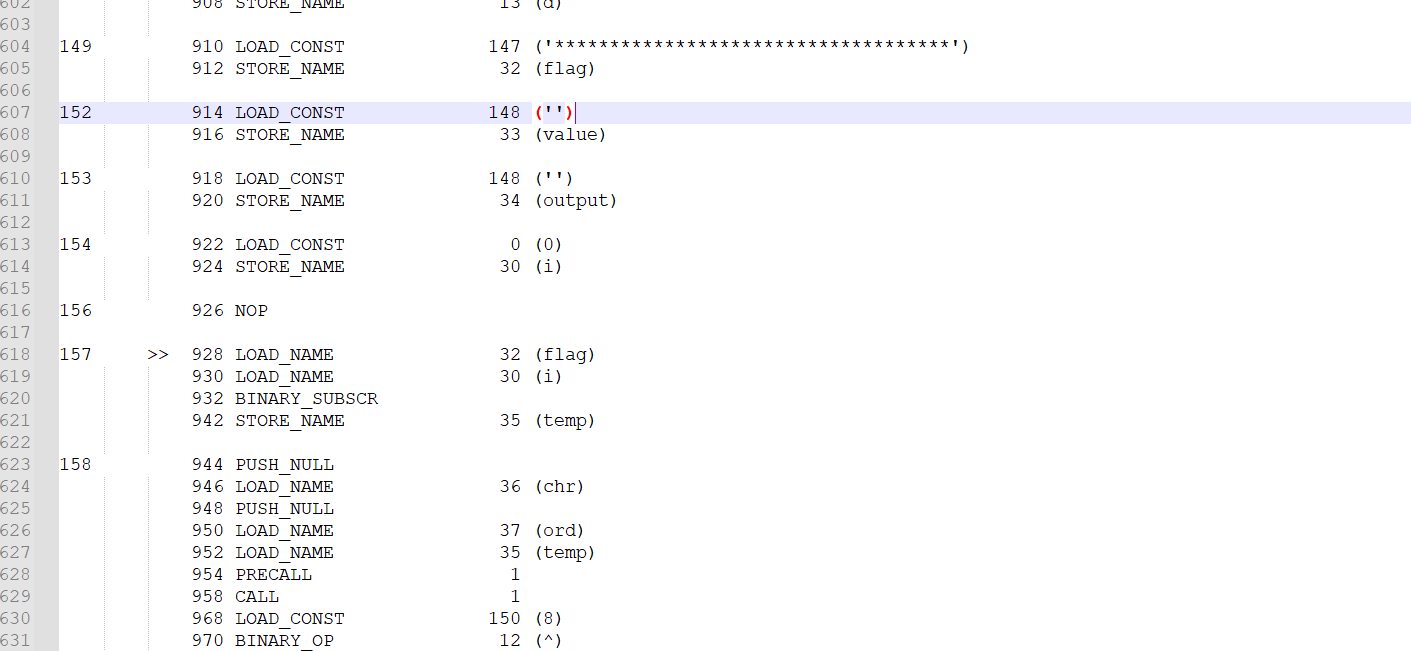
在txt的最后还附上了密文
1 | =1nb0A3b7AUQwB3b84mQ/E0MvJUb+EXbx5TQwF3bt52bAZncsd9c |
大概就是将密文运算后base64加密后再进行字符串替换
但是不知道哪些是本来就有的那些是替换而来的,选择爆破flag
1 | import base64 |
flag{5dcbafe63fbf3b7d8647c1aee650ae9c}
BadCoffee
javaScript
丢进phpstudy跑
index.html
1 | <script src="./BadCoffee.js" type="text/javascript" charset="utf-8"></script> |
直接动调
关键在于enc函数的两个for循环
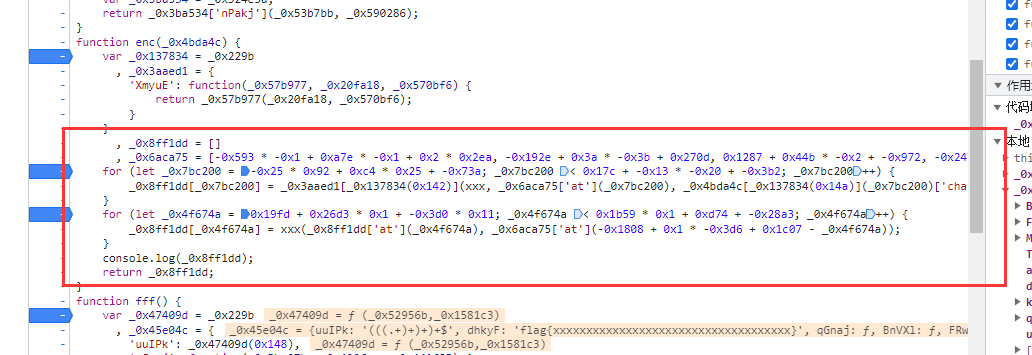
在调试的过程中发现程序只进行了异或操作,那么直接跑完整个加密然后再把加密后的字符串和输入异或即可得到用于加密的key
判断:
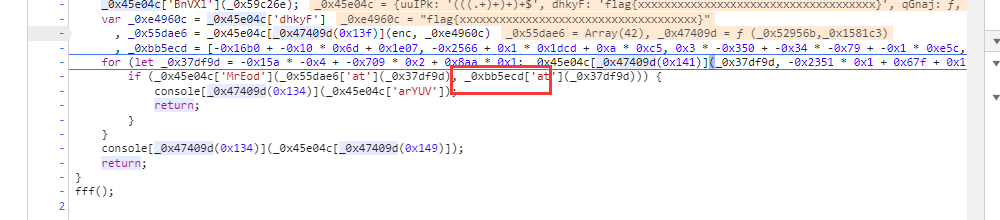
写脚本
1 | # 输入为 flag{xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx} |
flag{I_c0uld_neu3r_undeRstand_jvaVs3rIpt!}
Web&Assembly
wasm题,jeb倒是能打开但是反编译依托答辩
推荐ghidra并使用wasm插件
项目地址:https://github.com/nneonneo/ghidra-wasm-plugin
打开网址,题目已经给了足够的提示了

ghidra打开
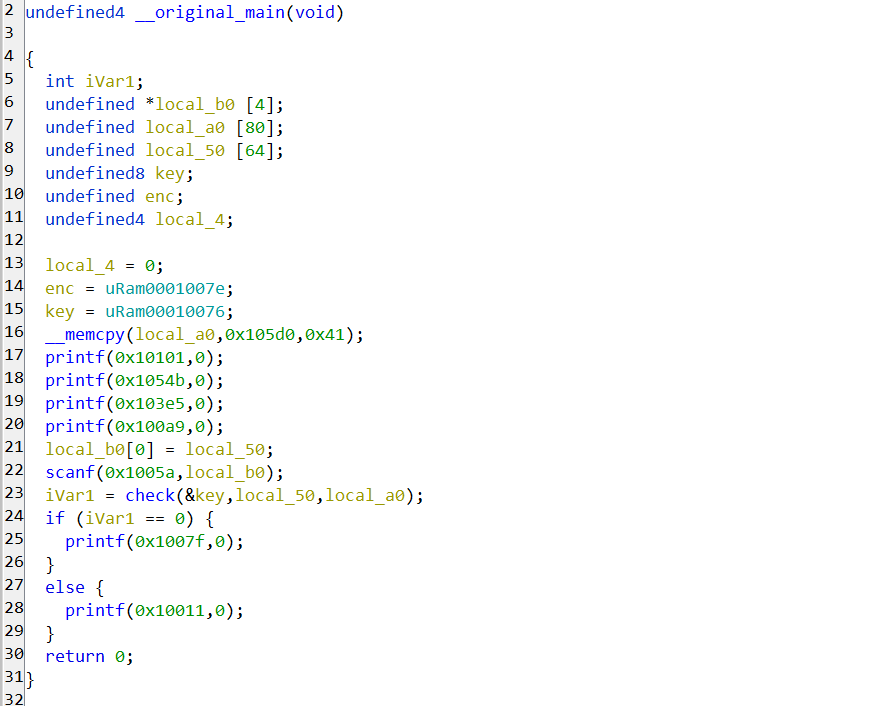
直接将输入和enc输入check函数
分析check函数
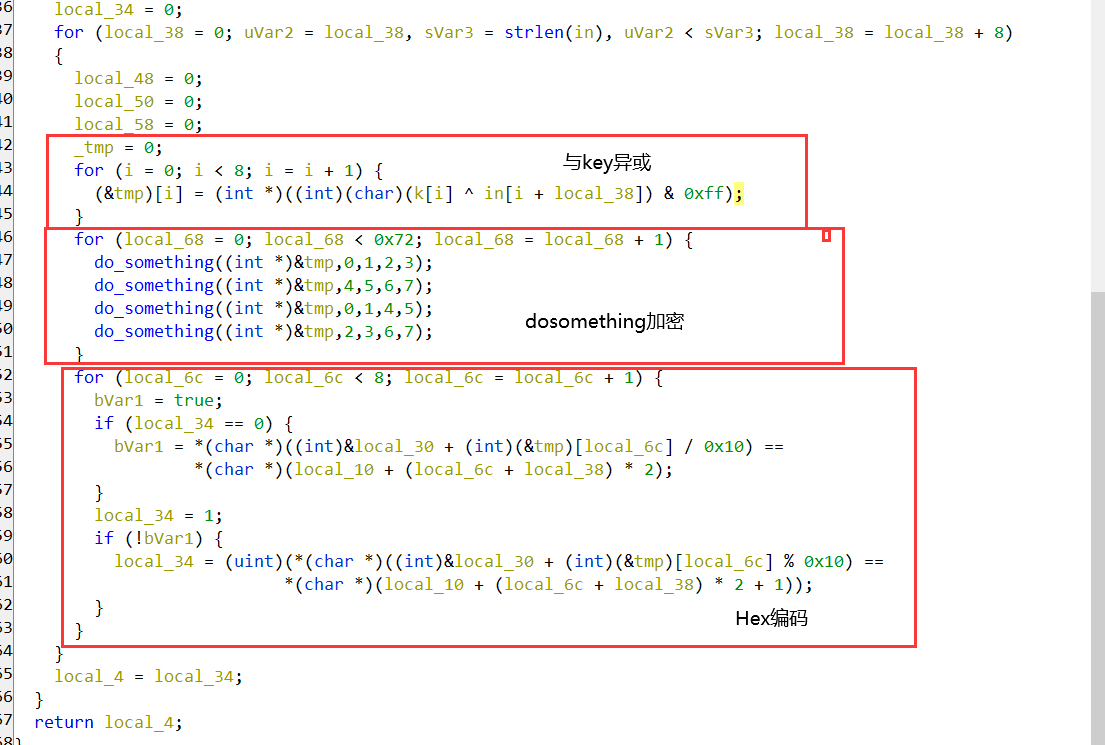
主要是分为三部,最后再与enc进行比较
接下来分析dosomething函数

简单的异或,但是要注意,+法的优先级高于位运算
最后即可写出脚本
1 | def dosomerthing(enc, a, b, c, d): |
flag{Y0u_Kn0w_W45M_n0w!!W0oO0ow}