UnCrackable-Level2
UnCrackable-Level2
jadx打开
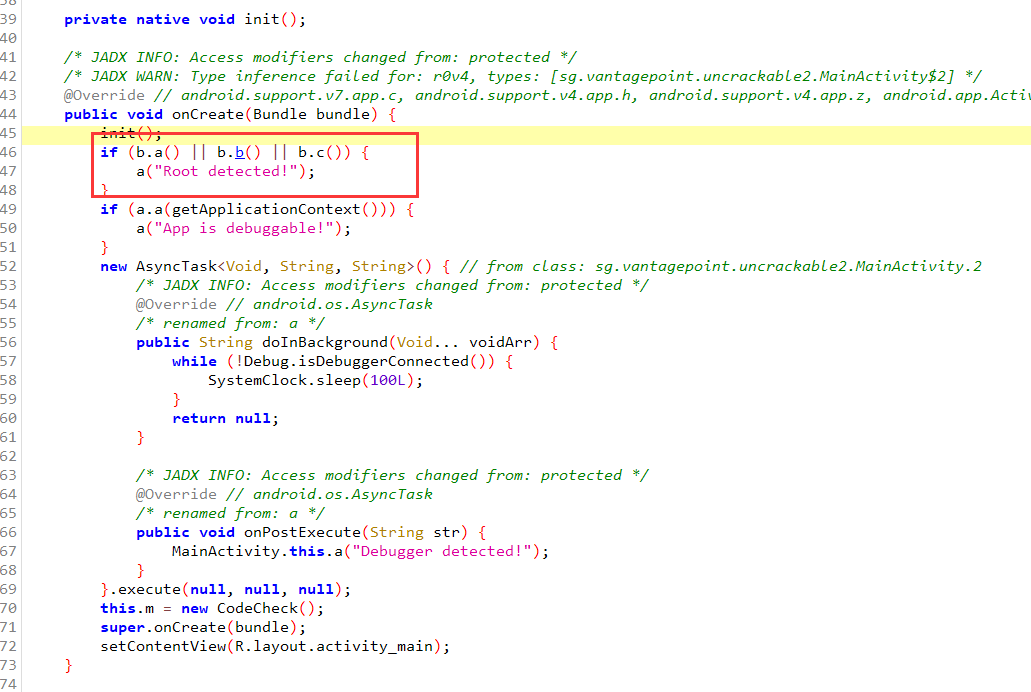
同样是检测root
init()函数是native,ida打开对应so
最终导向这个函数
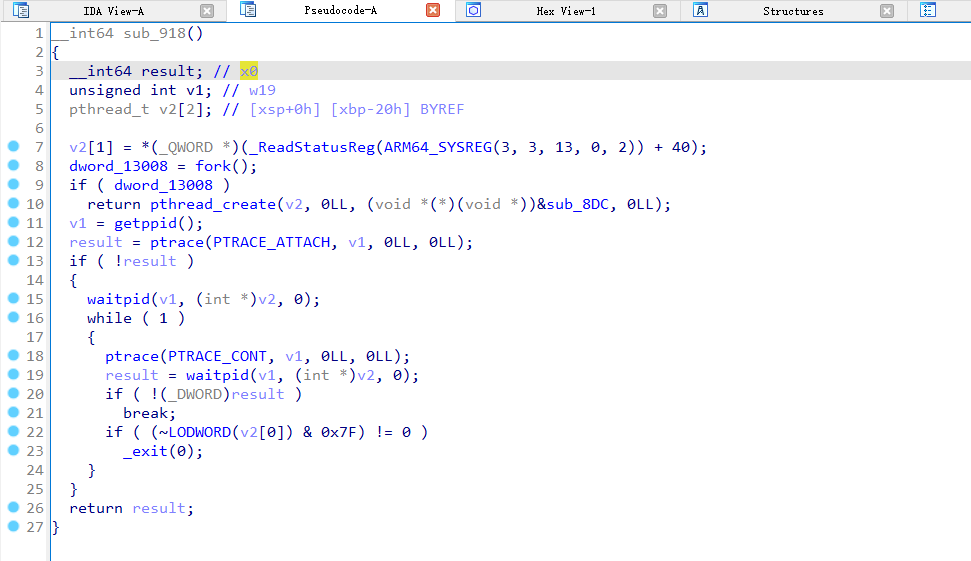
创建子进程,然后附加到父进程,因此不能运行后注入
利用spawn创建进程后hook
1 | console.log("Script loaded successfully "); |
1 | frida -U -f "owasp.mstg.uncrackable2" -l .\script.js --no-pause |
然后查看校验函数
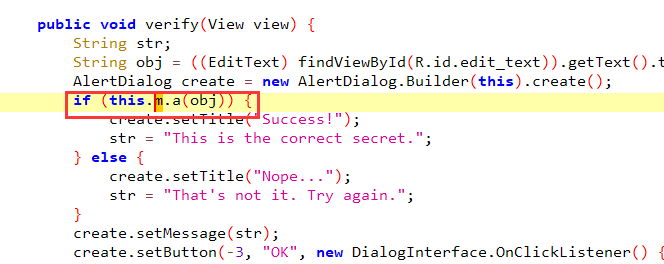
仍然是写在native里面
ida打开
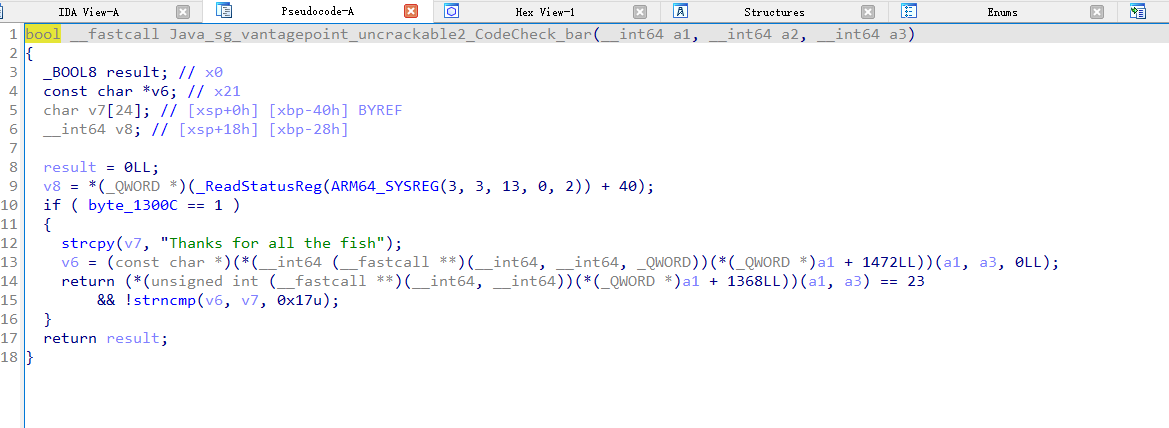
找到“Thanks for all the fish”
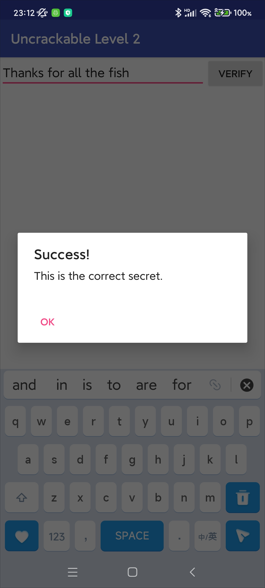
Thanks for all the fish