UnCrackable-Level1
UnCrackable-Level1
安卓逆向
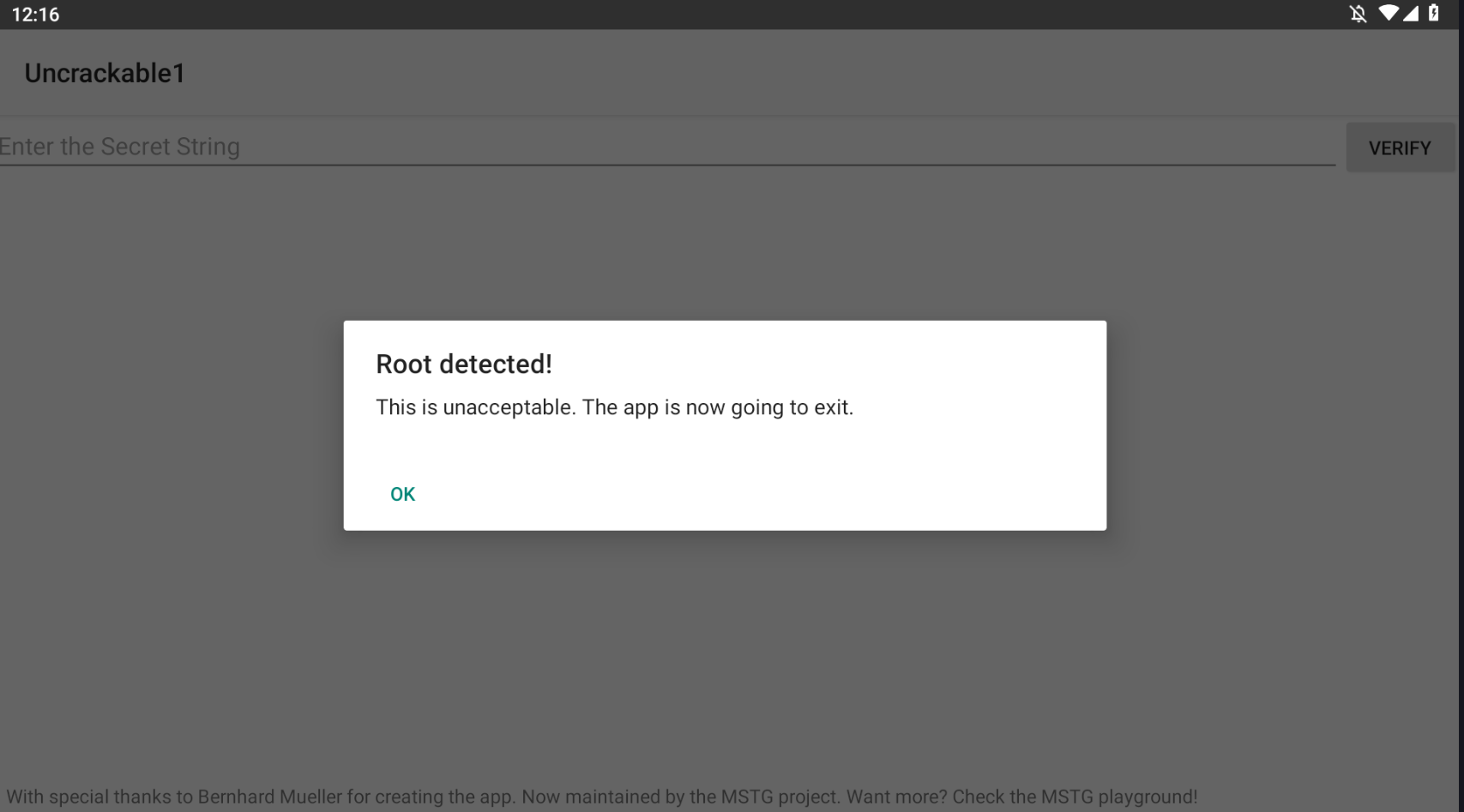
jadx打开
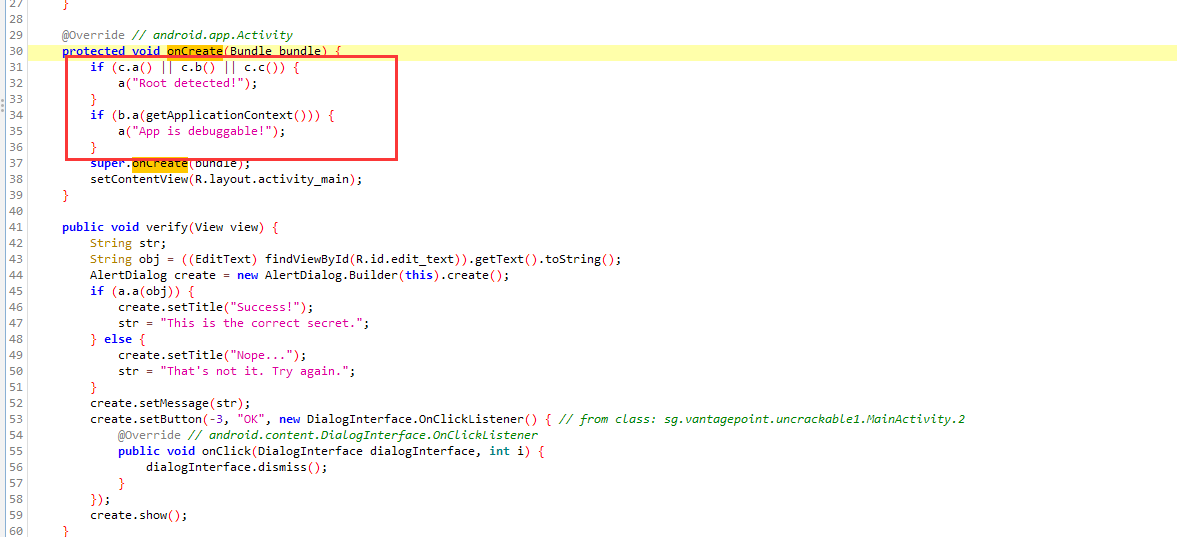
这里进行了校验
利用apktool进行修改后重打包
将这段删掉
1 | java -jar apktool.jar d UnCrackable-Level1.apk |
1 | java -jar apktool.jar b UnCrackable-Level1 |
然后再进行签名
首先生成自己的密钥
1 | keytool -genkey -alias demo.keystore -keyalg RSA -validity 40000 -keystore demo.keystore |
签名
1 | jarsigner -verbose -keystore demo.keystore UnCrackable-Level1.apk demo.keystore |
再安装,成功进入
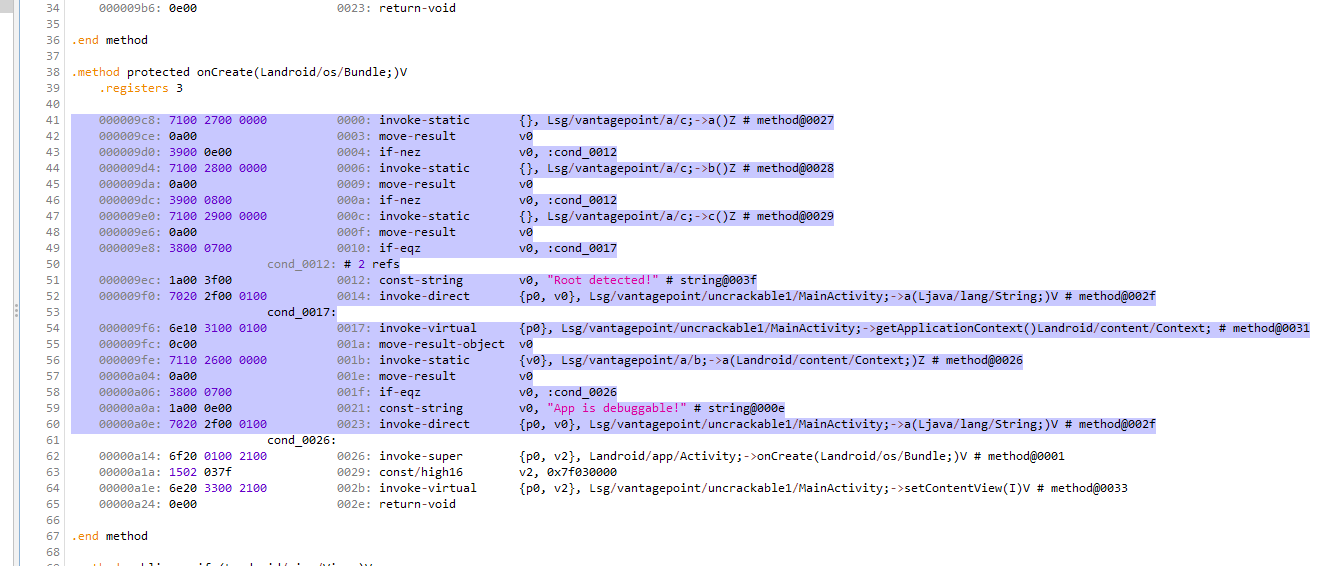
找到校验函数
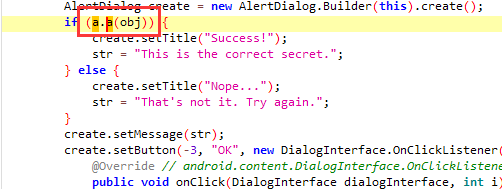
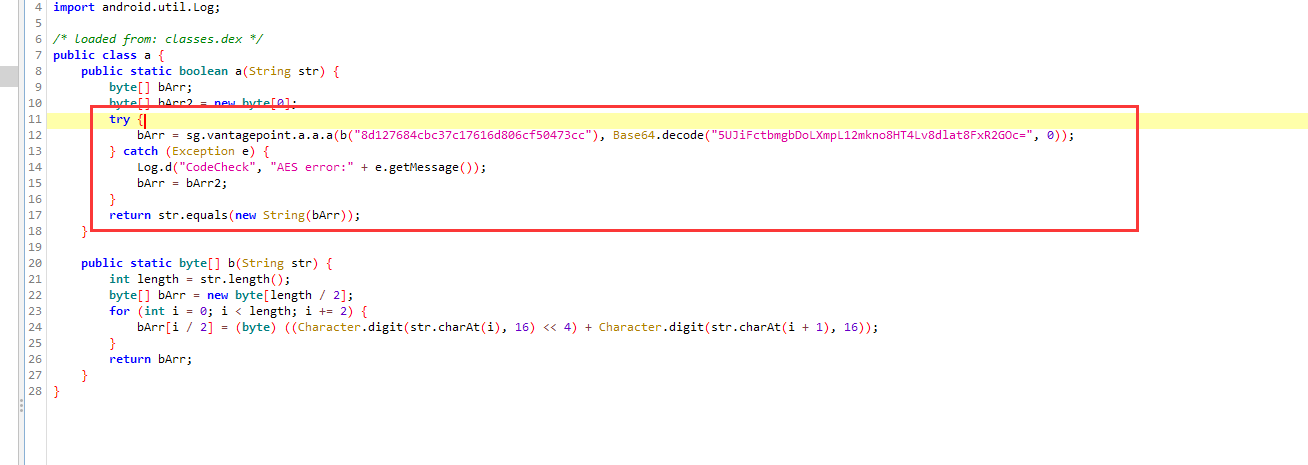
发现是AES+Base64
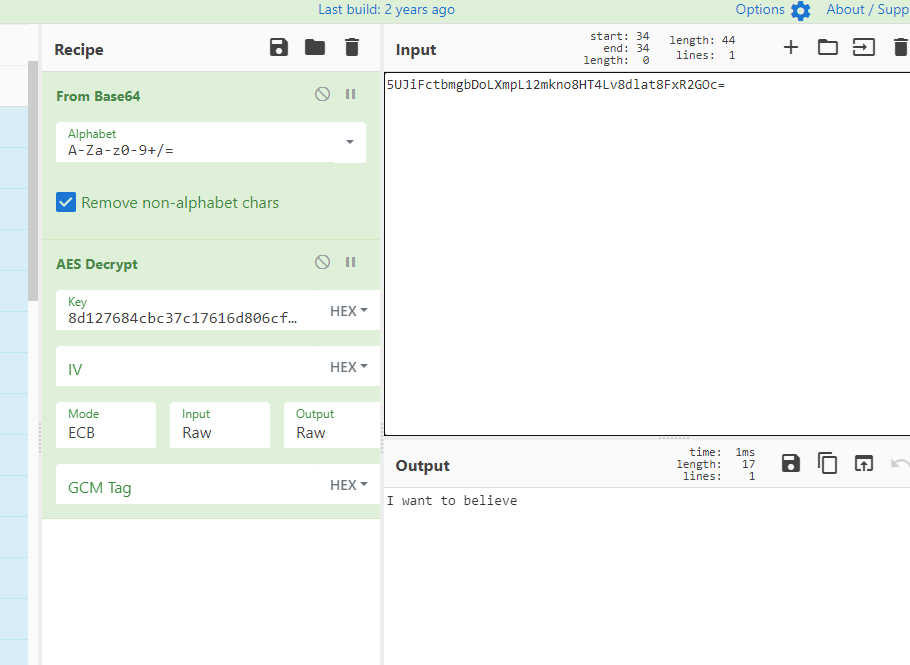
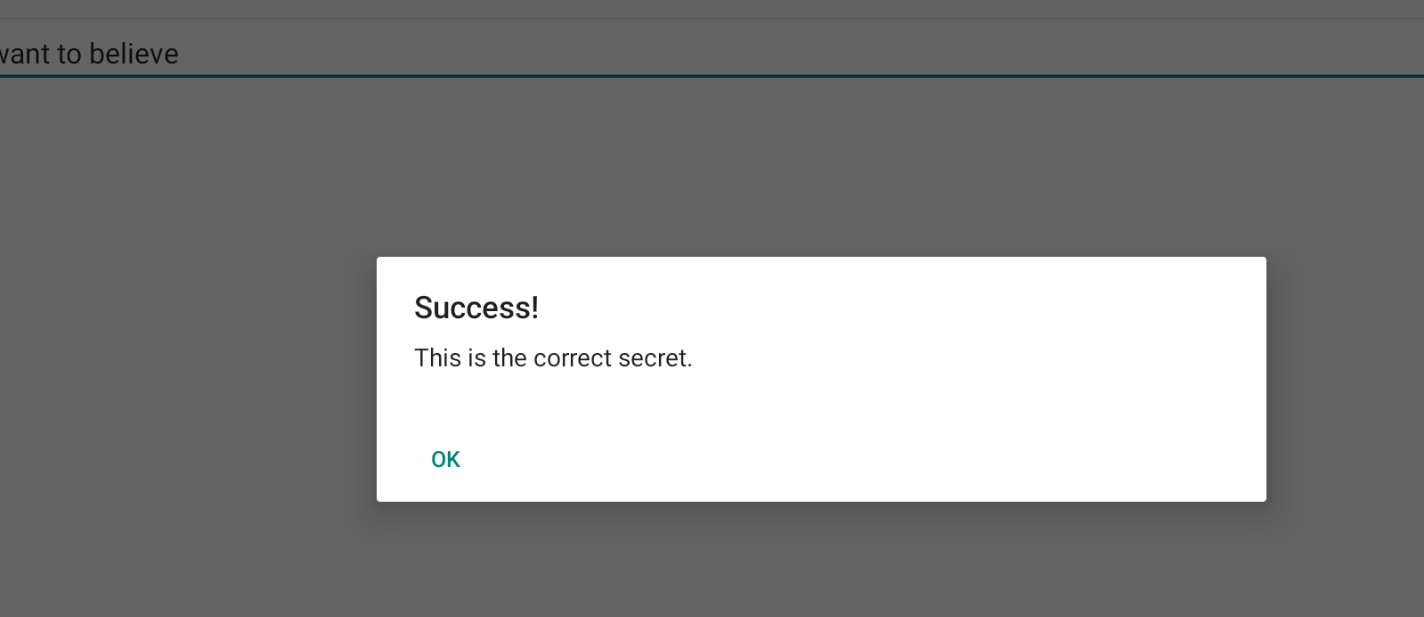
I want to believe
frida HOOK
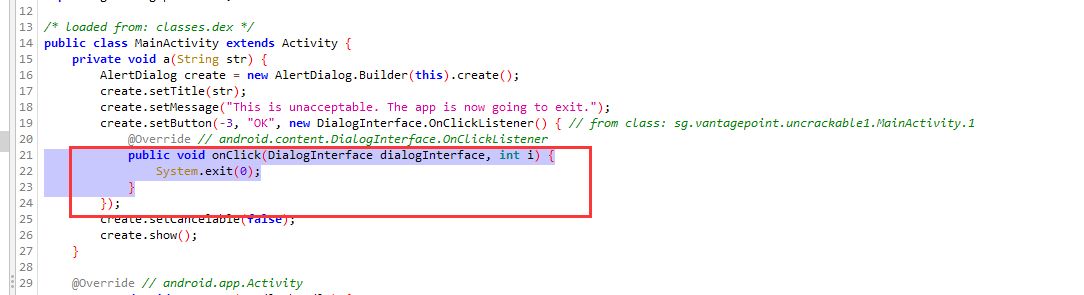
hook onClick函数使得点OK不退出
1 | console.log("Script loaded successfully "); |
1 | frida -UF -l .\script.js |
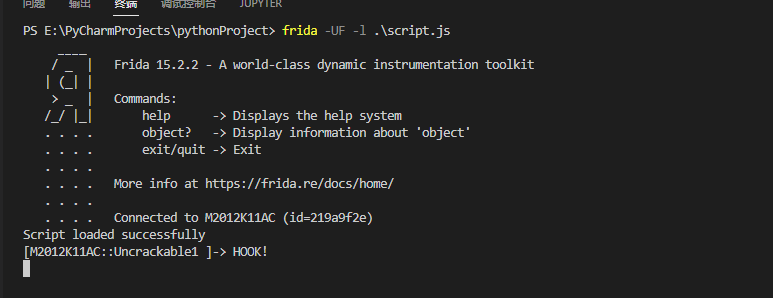
成功进入