ida32位打开
查看main函数
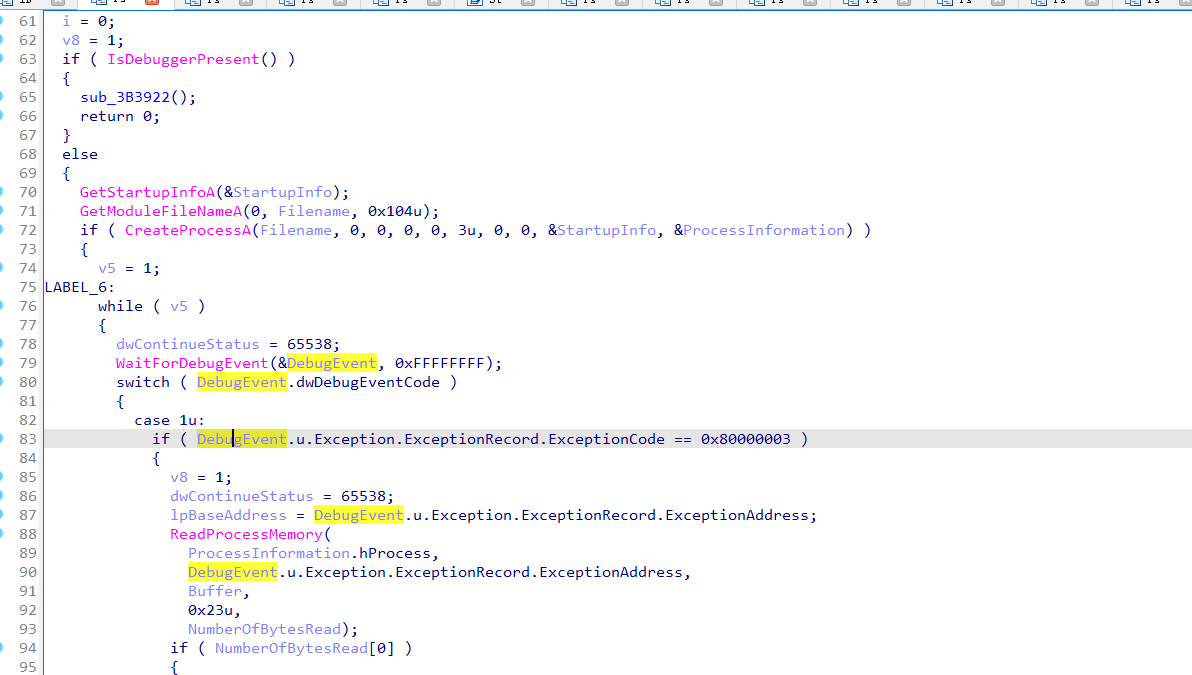
自我附加反调试
首先,主进程新建子进程,然后调试子进程。因为每一个进程同一时刻只能被一个调试器附加,因此无法调试子进程,只能静态分析。
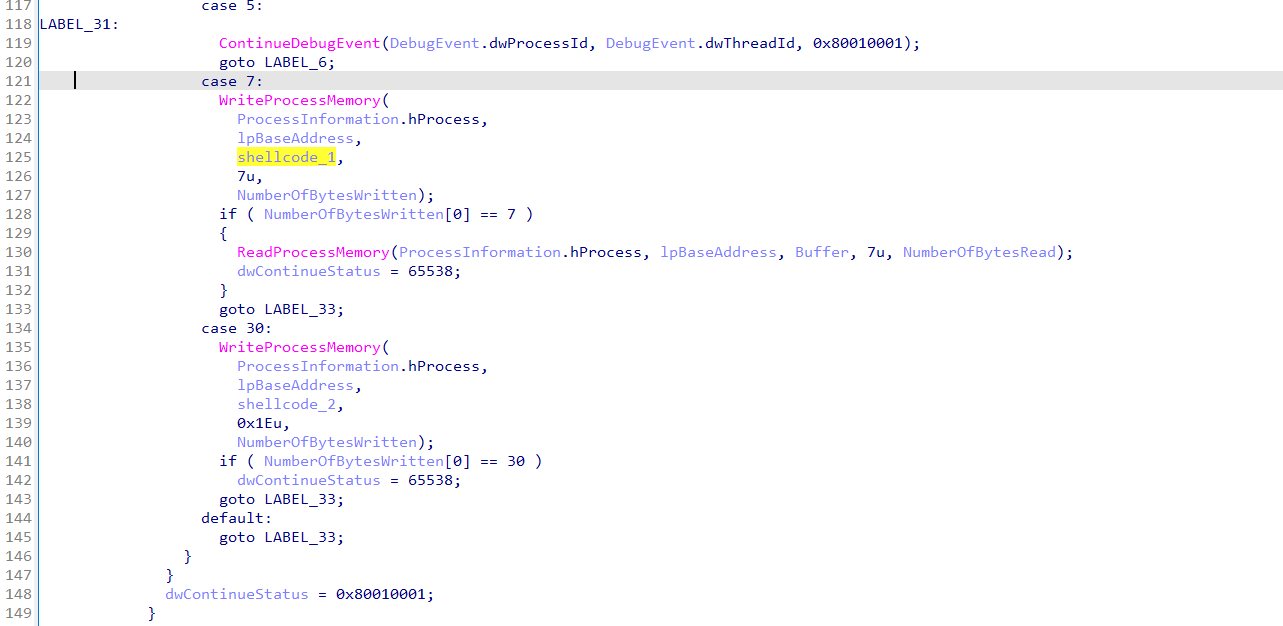
然后用主进程监控调试事件然后往子进程里面写数据
用keypatch将其还原后
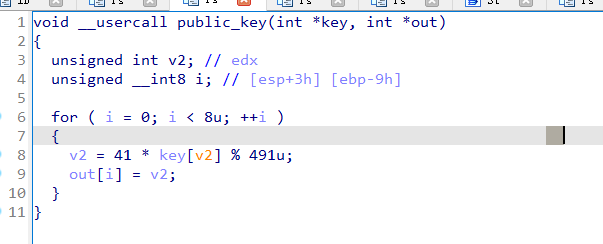
发现是个背包加密
首先初始化一个公钥
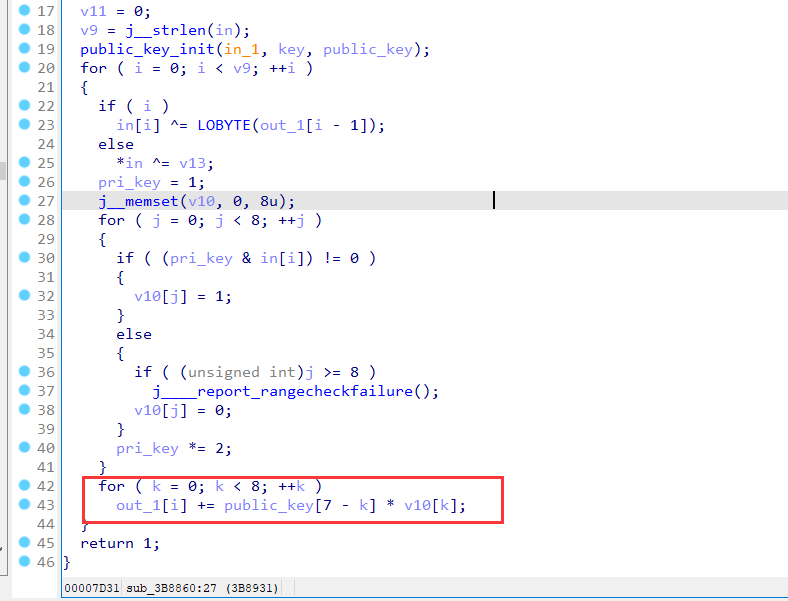
然后将明文每个字符的每个比特位(0或1)与公钥相乘并求和
写脚本
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 flag = [0 ] * 24 flag[0 ] = 0x3D1 flag[1 ] = 0x2F0 flag[2 ] = 0x52 flag[3 ] = 0x475 flag[4 ] = 0x1D2 flag[5 ] = 0x2F0 flag[6 ] = 0x224 flag[7 ] = 0x51C flag[8 ] = 0x4E6 flag[9 ] = 0x29F flag[10 ] = 0x2EE flag[11 ] = 0x39B flag[12 ] = 0x3F9 flag[13 ] = 0x32B flag[14 ] = 0x2F2 flag[15 ] = 0x5B5 flag[16 ] = 0x24C flag[17 ] = 0x45A flag[18 ] = 0x34C flag[19 ] = 0x56D flag[20 ] = 0xA flag[21 ] = 0x4E6 flag[22 ] = 0x476 flag[23 ] = 0x2D9 key = [2 , 3 , 7 , 14 , 30 , 57 , 120 , 251 ] v13 = 0x1234 inv = 12 for i in range (len (flag)): w = (inv * flag[i]) % 491 x = "" for j in range (8 ): if key[7 - j] > w: x = "0" + x else : x = "1" + x w -= key[7 - j] x = int (x, 2 ) if i == 0 : x = x ^ 0x1234 else : x = x ^ flag[i - 1 ] print (chr (x & 0xff ), end="" )
swpuctf{y0u_@re_s0_coo1}