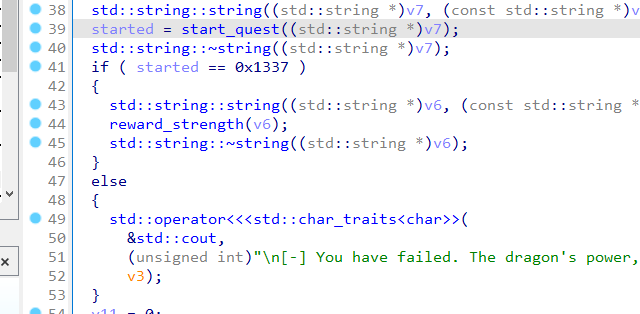
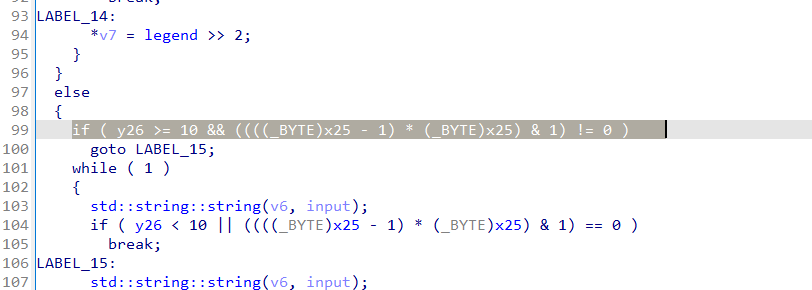
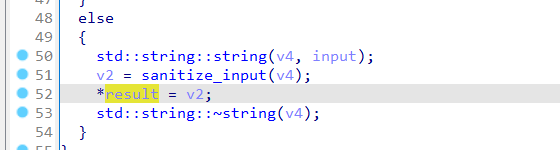
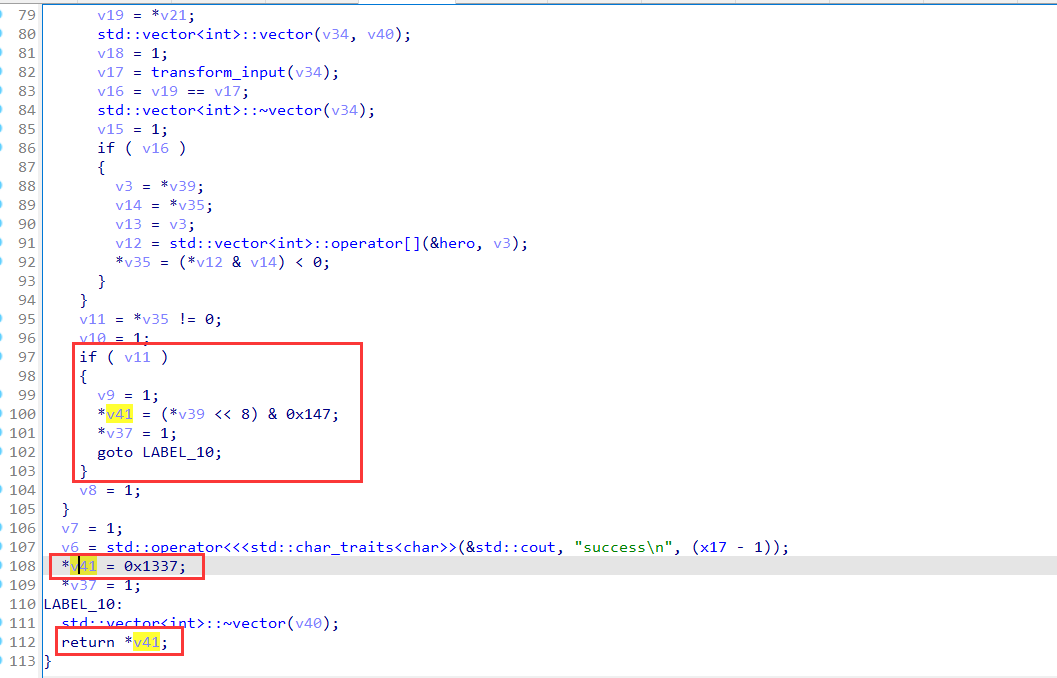
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
| from ida_bytes import get_bytes, patch_bytes
def compare1(buff, addr):
enc = [0x8B, 0x04, 0x25, 0xE0, 0x03, 0x61, 0x00, 0x8B]
eax = [0xB8, 0x00]
for i in range(8):
if buff[i] != enc[i]:
return 0
tmp = addr + 25
patch_bytes(tmp, bytes(eax))
def compare2(buff, addr):
enc = [0x8B, 0x0C, 0x25, 0xE0, 0x03, 0x61, 0x00, 0x8B]
ecx = [0xB9, 0x00, 0x00, 0x00, 0x00, 0x90]
for i in range(8):
if buff[i] != enc[i]:
return 0
tmp = addr + 25
patch_bytes(tmp, bytes(ecx))
def compare3(buff, addr):
enc = [0x44, 0x8B, 0x0C, 0x25, 0xE0, 0x03, 0x61, 0x00, 0x44]
r9d = [0x41, 0xB9, 0x00, 0x00, 0x00, 0x00, 0x90]
for i in range(len(enc)):
if buff[i] != enc[i]:
return 0
tmp = addr + 29
patch_bytes(tmp, bytes(r9d))
if __name__ == '__main__':
start_addr = 0x00404350
end_addr = 0x00404AD5
for i in range(start_addr, end_addr, 1):
buf = get_bytes(i, 9)
compare1(buf, i)
compare2(buf, i)
compare3(buf, i)
|