hgame2023
HGAME2023
by 没有眼的鱼
Week1
test_your_IDA
ida64位打开
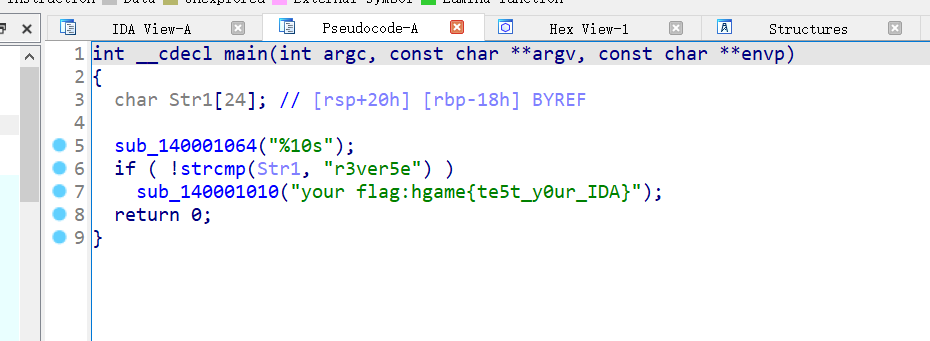
1 | hgame{te5t_y0ur_IDA} |
easyasm

核心是Str[i] ^= 0x33
1 | flag = [ |
1 | hgame{welc0me_t0_re_wor1d!} |
easyenc
ida64位打开

核心逻辑是先异或0x32再减去86
留意v8是以小端序的形式储存密文
写脚本
1 | flag = [ |
1 | hgame{4ddit1on_is_a_rever5ible_0peration} |
a_cup_of_tea
ida64位

每8位一组进行加密

改了delta的tea加密
写脚本
1 |
|
1 | hgame{Tea_15_4_v3ry_h3a1thy_drlnk} |
encode
ida32位
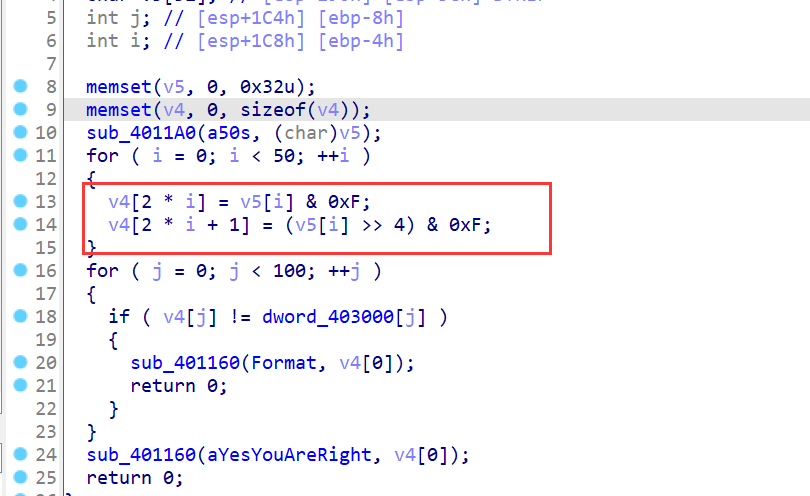
就单纯的把v5的前四位和后四位拆开了
写脚本
1 | flag = [ |
1 | hgame{encode_is_easy_for_a_reverse_engineer} |
Week2
before_main
ida64位打开
根据提示很明显有函数在main之前运行了
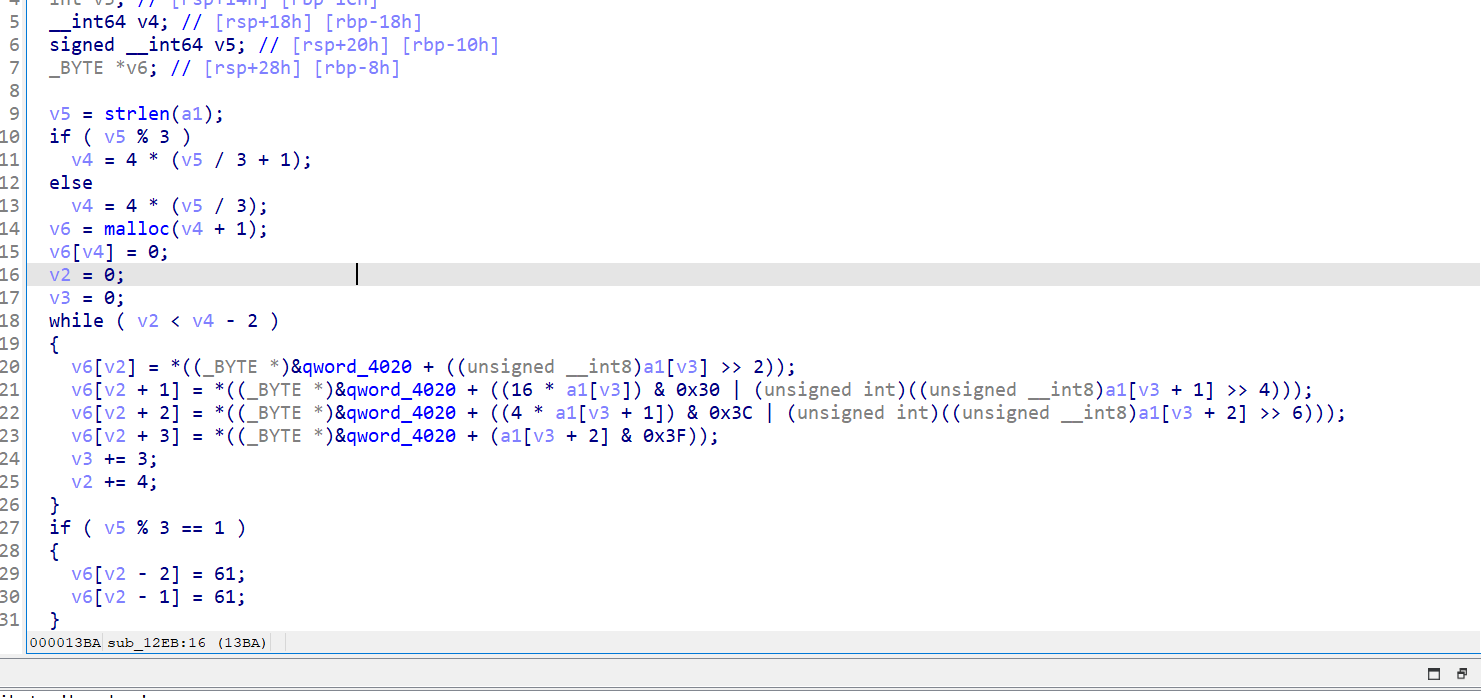
结合base64,猜测可能是该表,对qword_4020交叉引用
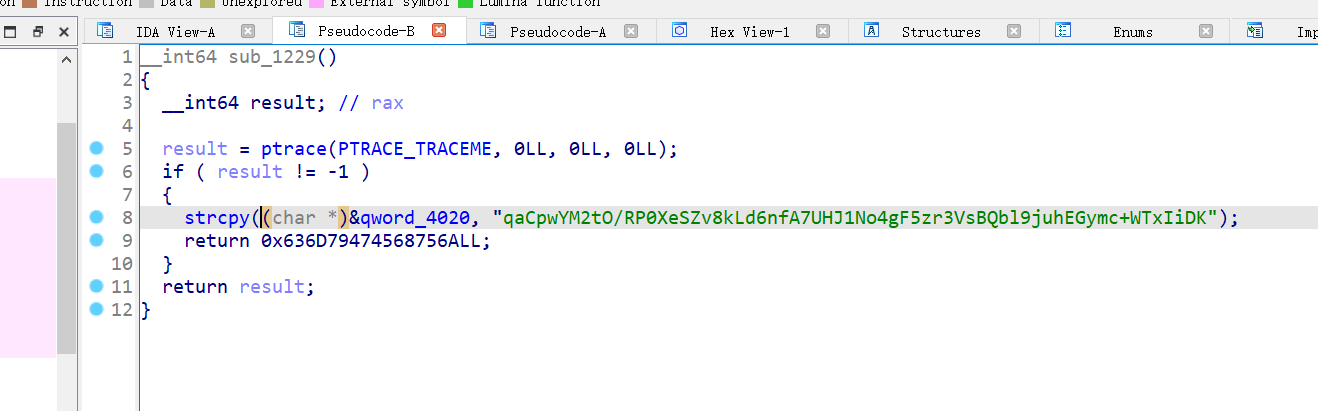
找到了该函数,换表base64
1 | hgame{s0meth1ng_run_befOre_m@in} |
math
ida64位打开
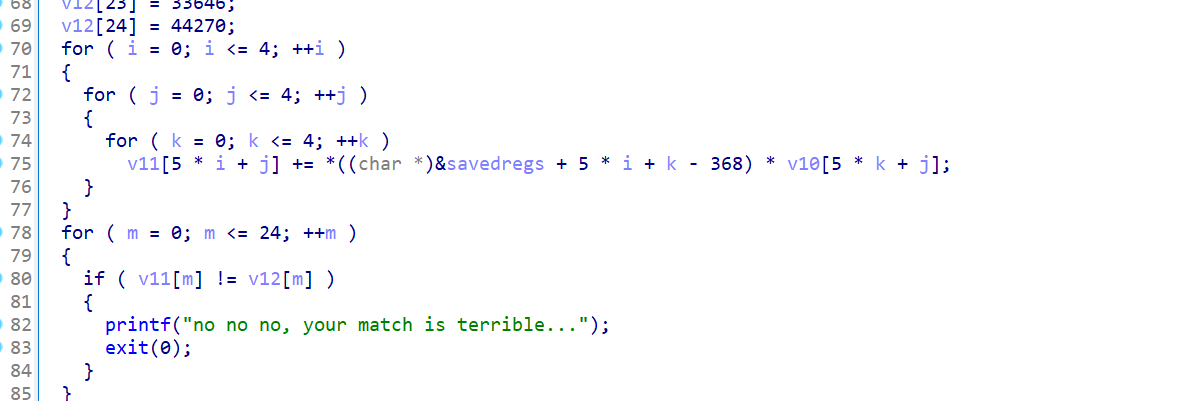
动态调试的话会发现这个savedregs - 368指向的就是输入的开头
下面三层循环很明显就是矩阵乘法
v12 == input * v10
用z3写脚本
1 | from z3 import * |
1 | hgame{y0ur_m@th_1s_gO0d} |
stream
python编译的exe
pyinstxtractor.py后再把pyc丢去反编译
1 | #!/usr/bin/env python |
直接写脚本就行了
但是要注意这个base64,一开始我以为这个encode decode只是编码和字符的转换。没想到他base64加密的是字符串编码后的数据
1 | import base64 |
1 | hgame{python_reverse_is_easy_with_internet} |
VidarCamera
雷电模拟器
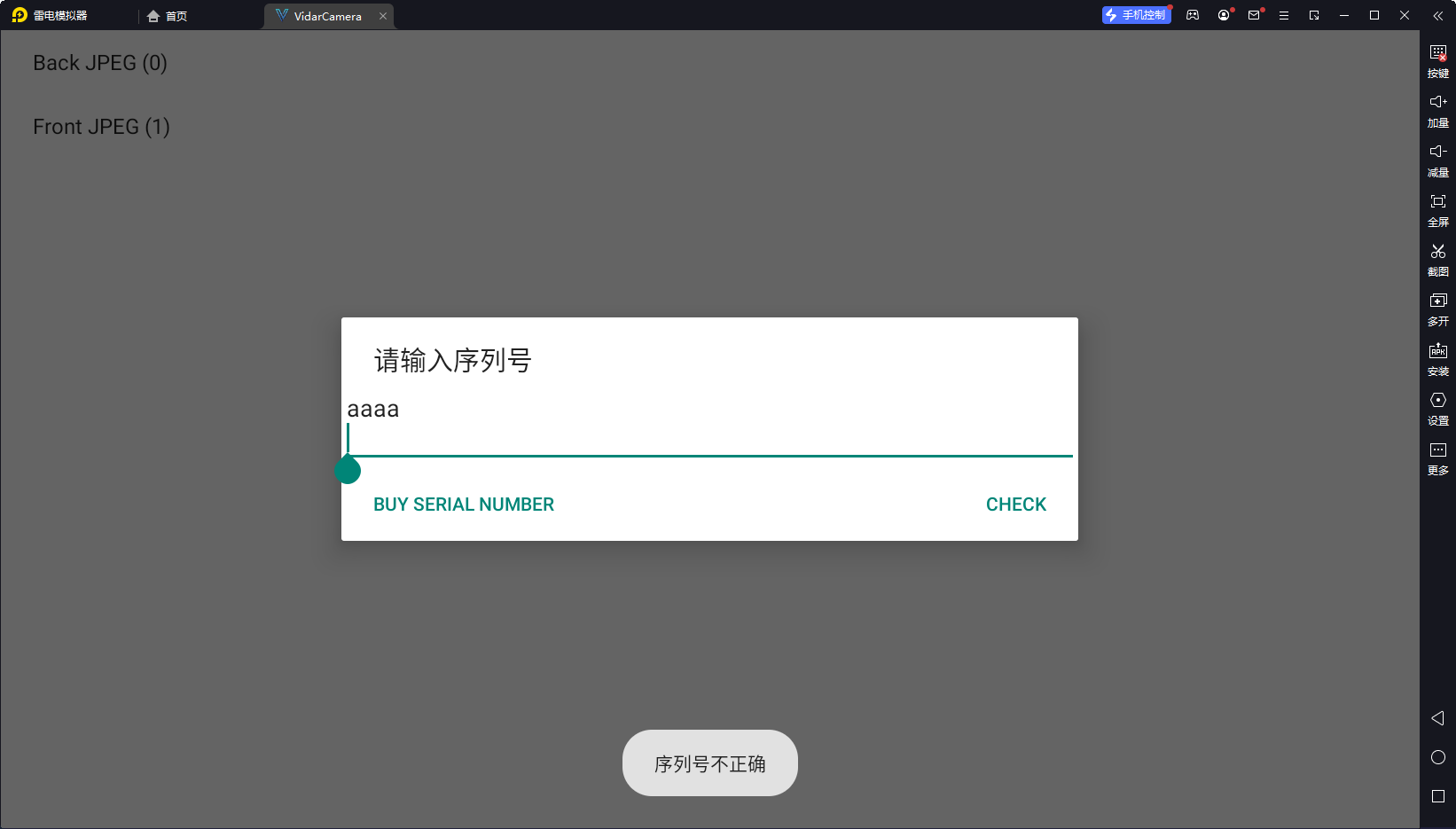
jeb打开,直接查找字符串找到序列号不正确
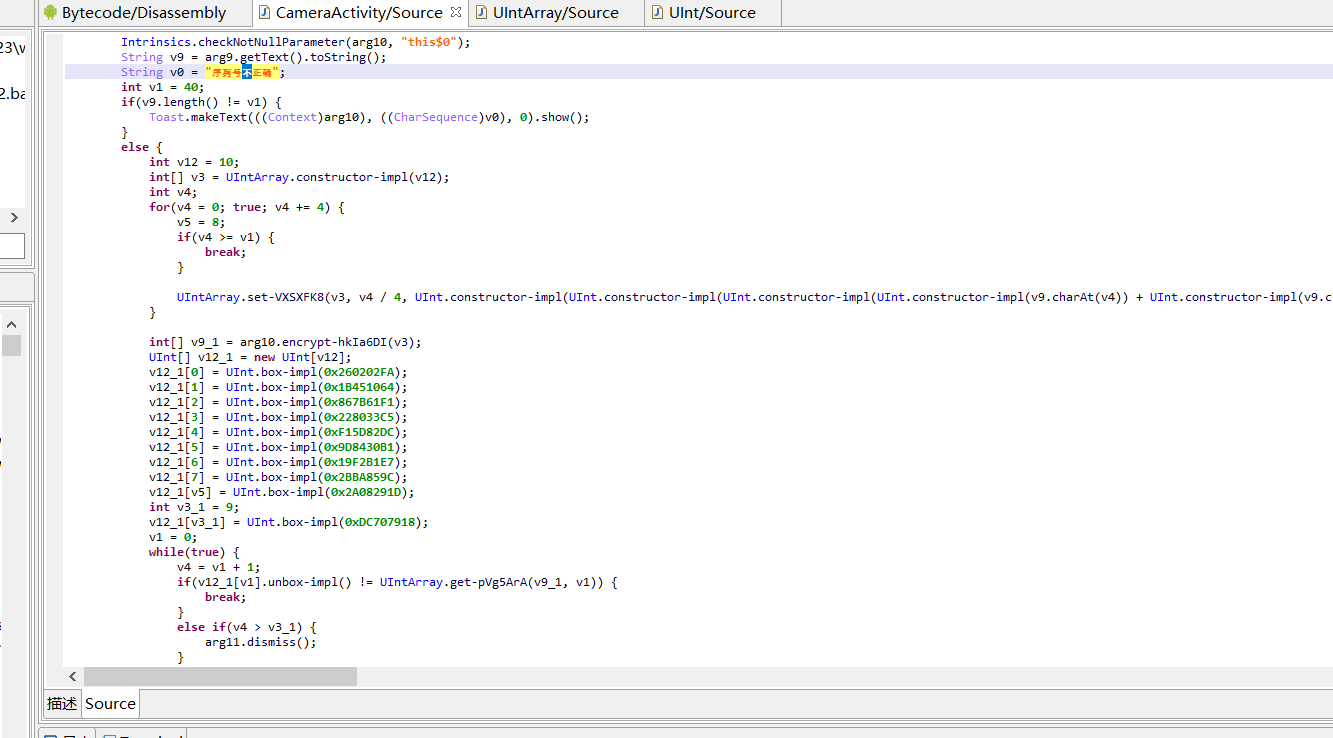
找到flag
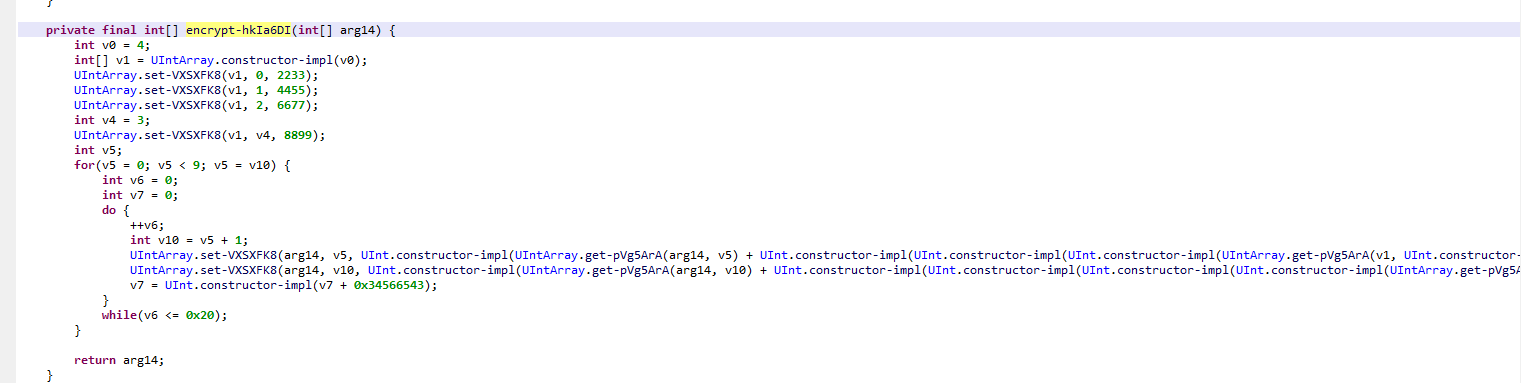
点开加密函数,魔改后的xtea
要注意轮次,一方面是嵌套的得从最后一组开始解密,另一方面下面的while总共有33轮
写脚本
1 |
|
1 | hgame{d8c1d7d34573434ea8dfe5db40fbb25c0} |
Week3
patchme
1 |
|
1 | flag = [ |
hgame{You_4re_a_p@tch_master_0r_reverse_ma5ter}
kunmusic
1 | import re |
hgame{z3_1s_very_u5eful_1n_rever5e_engin3ering}
cpp
1 | b = [ |
hgame{Cpp_1s_much_m0r3_dlff1cult_th4n_C}