1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
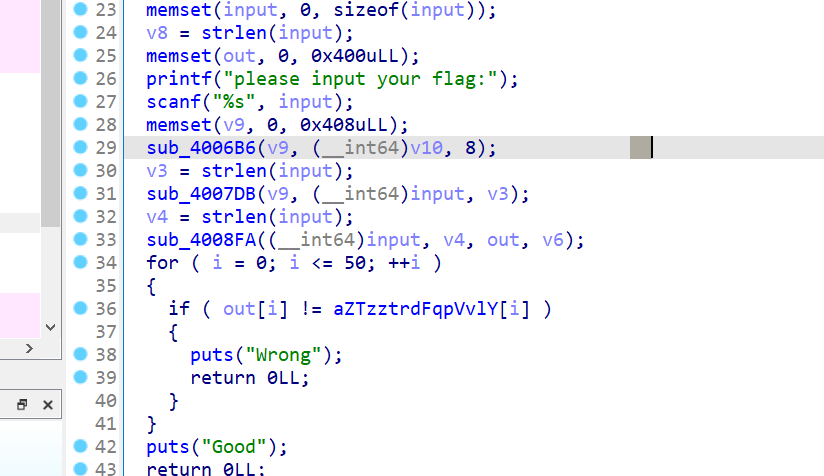
23
24
25
26
27
28
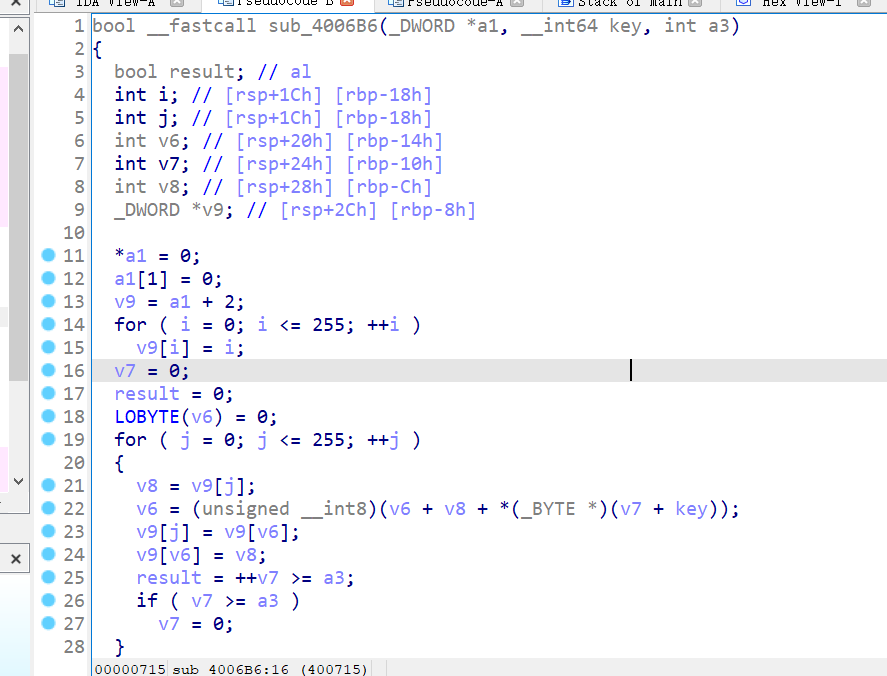
29
30
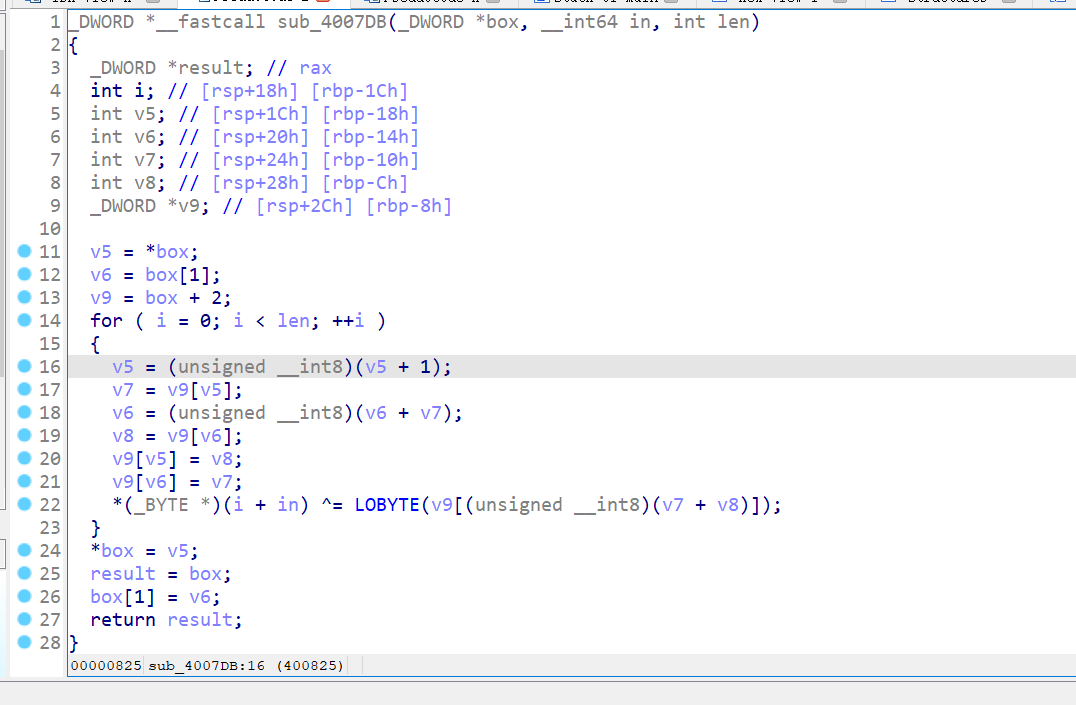
31
32
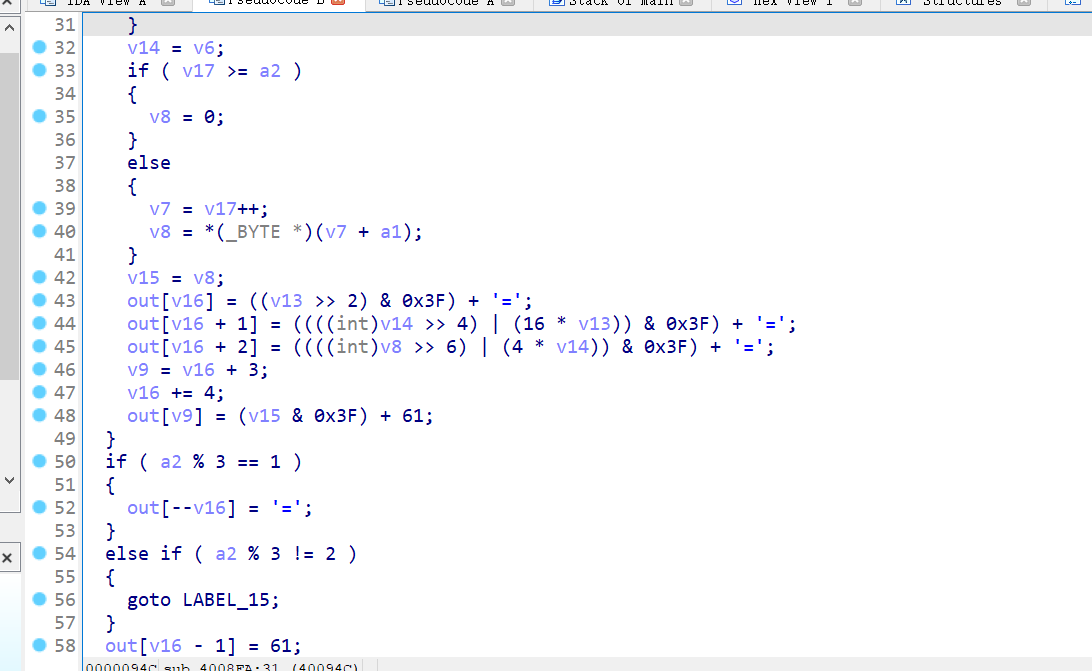
33
34
35
36
37
38
39
40
41
42
43
| from Crypto.Cipher import DES
import base64
enc = [0x5a, 0x60, 0x54, 0x7A, 0x7A, 0x54, 0x72, 0x44,
0x7C, 0x66, 0x51, 0x50, 0x5B, 0x5F, 0x56, 0x56,
0x4C, 0x7C, 0x79, 0x6E, 0x65, 0x55, 0x52, 0x79,
0x55, 0x6D, 0x46, 0x6B, 0x6C, 0x56, 0x4A, 0x67,
0x4C, 0x61, 0x73, 0x4A, 0x72, 0x6F, 0x5A, 0x70,
0x48, 0x52, 0x78, 0x49, 0x55, 0x6C, 0x48, 0x5C,
0x76, 0x5A, 0x45, 0x3D]
h = []
for i in range(0, len(enc), 4):
h.append(((((enc[i] - 0x3d) & 0x3f) << 2) | (((enc[i + 1] - 0x3d) & 0x30) >> 4)))
h.append((((enc[i + 1] - 0x3d) & 0xf) << 4) | (((enc[i + 2] - 0x3d) & 0x3c) >> 2))
h.append((((enc[i + 2] - 0x3d) & 0x3) << 6) | ((enc[i + 3] - 0x3d) & 0x3f))
key = [16, 32, 48, 48, 32, 32, 16, 64]
box = [0] * 256
for i in range(256):
box[i] = i
v6 = 0
for i in range(256):
v8 = box[i]
v6 = (v6 + v8 + key[i % 8]) & 0xff
box[i] = box[v6]
box[v6] = v8
v5 = 0
v6 = 0
for i in range(len(h)):
v5 = (v5 + 1) % 256
v7 = box[v5]
v6 = (v6 + v7) % 256
v8 = box[v6]
box[v5] = v8
box[v6] = v7
h[i] ^= (box[(v7 + v8) % 256])
for i in h:
print(chr(i), end="")
|