FlareOn2_very_success
[FlareOn2]very_success
32位ida
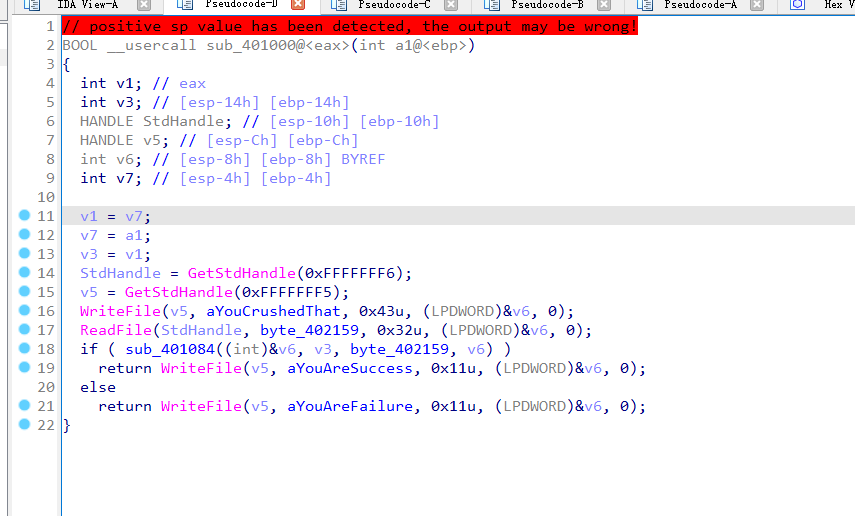
很明显一个输入加判断
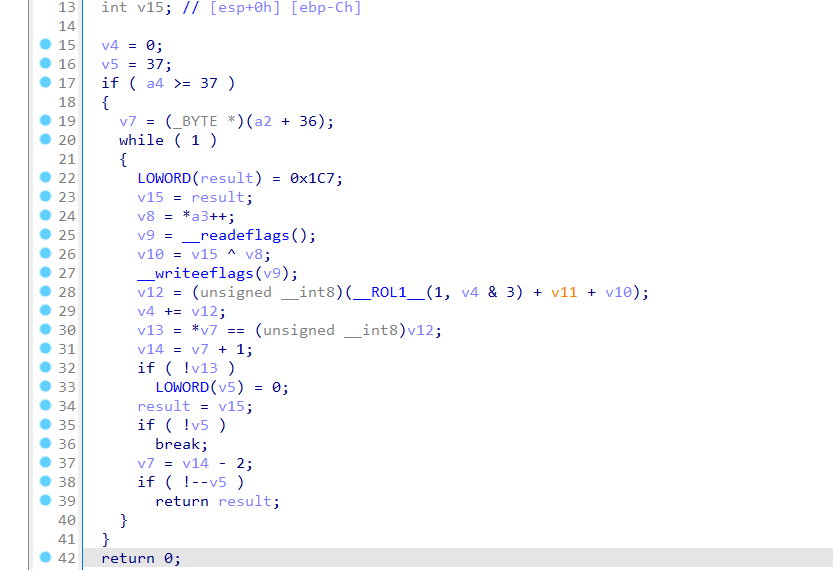
简单的加密,唯一要注意的就是v11
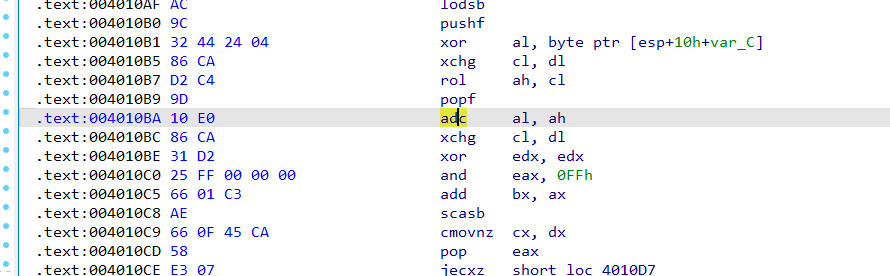
看汇编或者动调发现,因为这个popf的原因,使得cf标志位为1,adc是带进位加法,也就是说这个v11恒为1
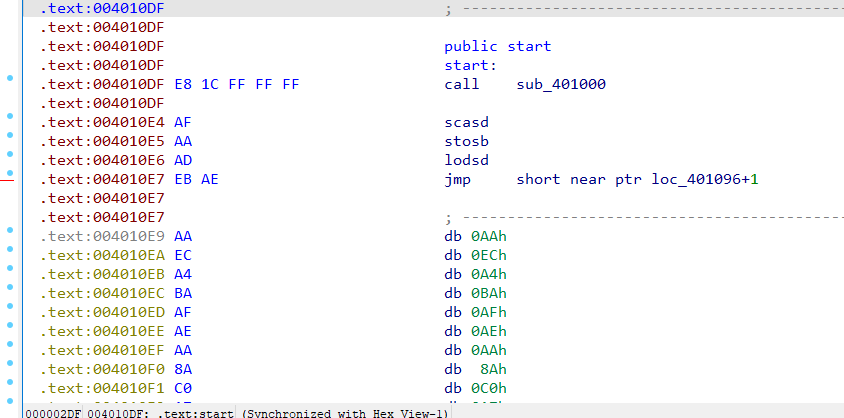
至于a3则靠动调直接得出,只不过a3有部分数据有可能会被ida错误的识别成代码
写脚本
1 | flag = [ |
32位ida

很明显一个输入加判断

简单的加密,唯一要注意的就是v11

看汇编或者动调发现,因为这个popf的原因,使得cf标志位为1,adc是带进位加法,也就是说这个v11恒为1
至于a3则靠动调直接得出,只不过a3有部分数据有可能会被ida错误的识别成代码

写脚本
1 | flag = [ |