swpu2019 ReverseMe
[SWPU2019]ReverseMe
ida 32 位
程序有点复杂,要靠动调来猜测
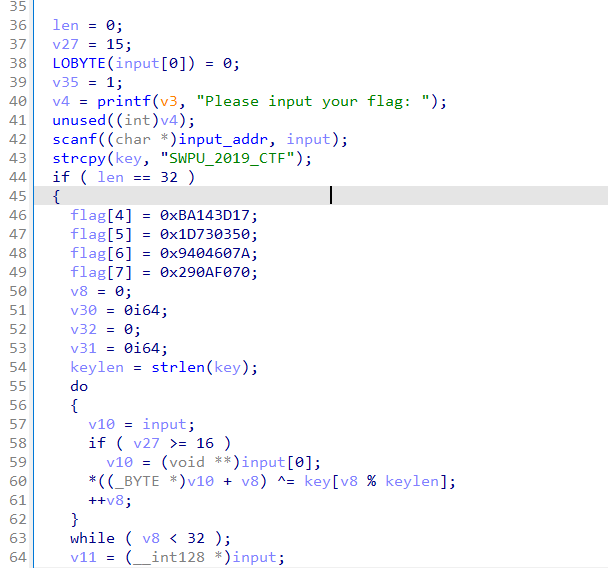
32位输入
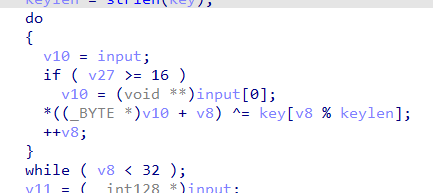
先和key异或
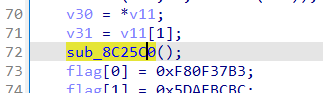
函数加密后在和flag比较
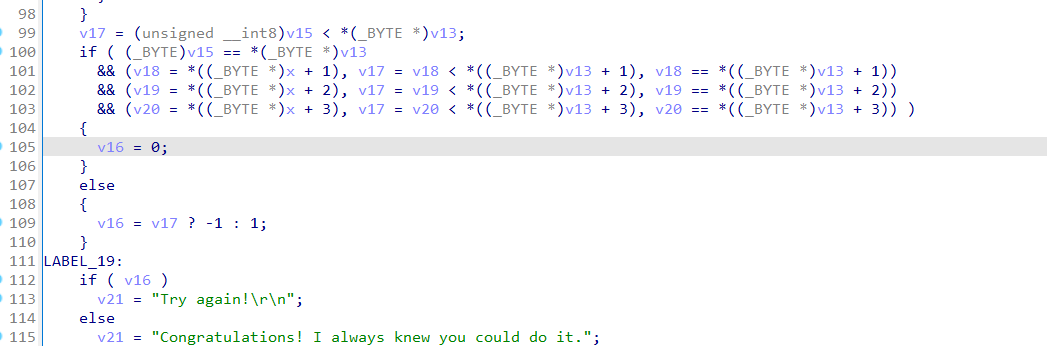
关键在于如何处理加密函数
函数很复杂但真正影响到的只有这个异或
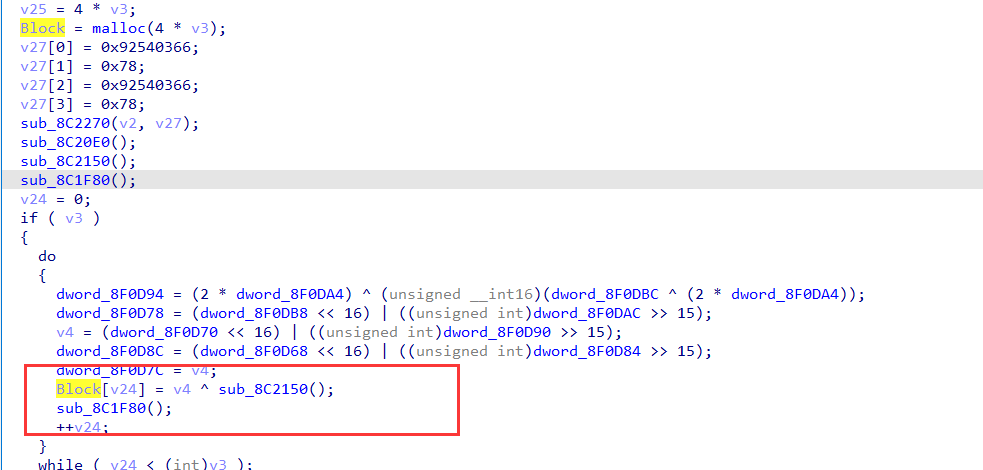
异或的值是动态生成的,直接动调
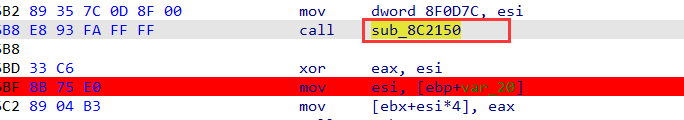
调用这个函数会生成一个值,返回到eax寄存器里面
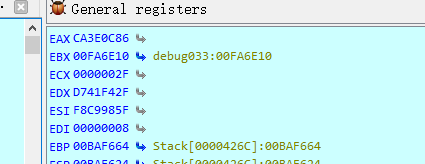
eax中的值就是异或的值
写脚本
1 | enc = [ |
1 | flag{Y0uaretheB3st!#@_VirtualCC} |
ida 32 位
程序有点复杂,要靠动调来猜测

32位输入
先和key异或

函数加密后在和flag比较


关键在于如何处理加密函数
函数很复杂但真正影响到的只有这个异或

异或的值是动态生成的,直接动调

调用这个函数会生成一个值,返回到eax寄存器里面

eax中的值就是异或的值
写脚本
1 | enc = [ |
1 | flag{Y0uaretheB3st!#@_VirtualCC} |