NewStar2022wp
Week 2
FindME
ida64打开
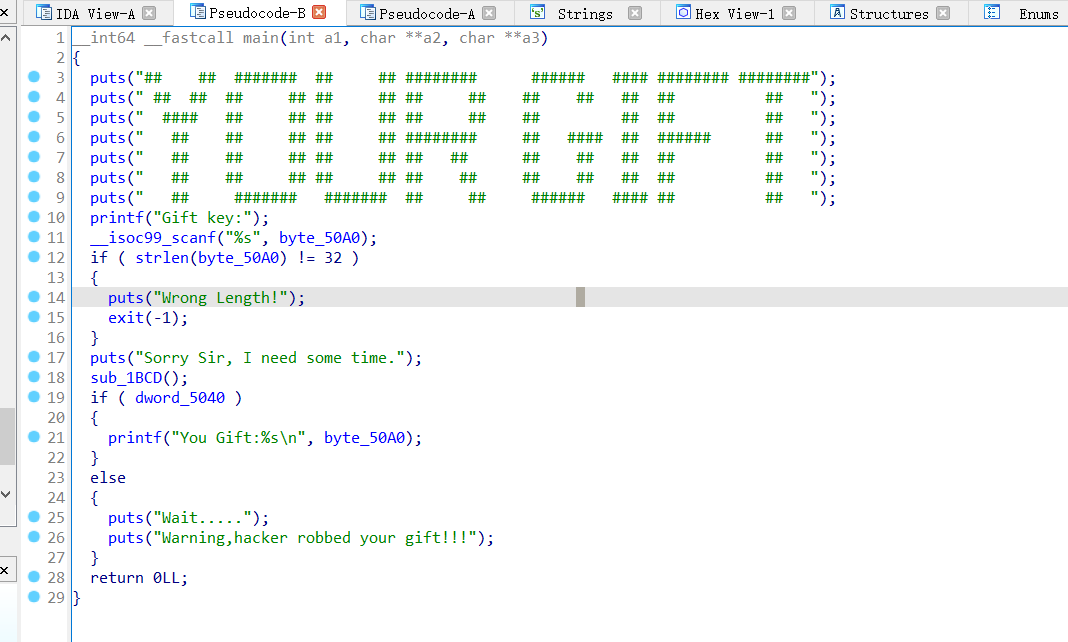
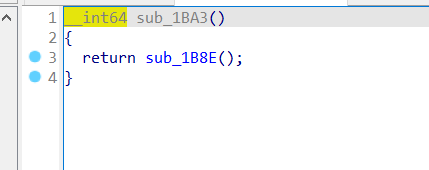
打开sub_1BCD函数 发现是一堆return 的函数
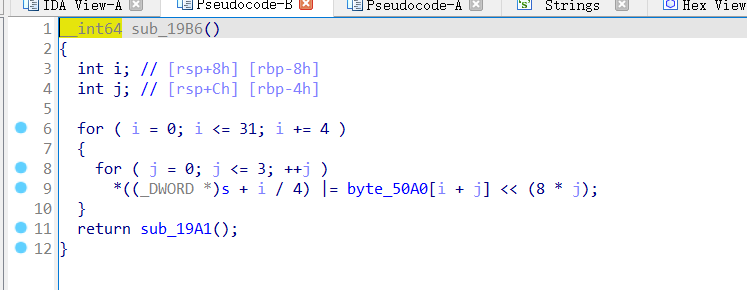
找到其中一个有用的函数之后对 s 按 x直接查询交叉引用
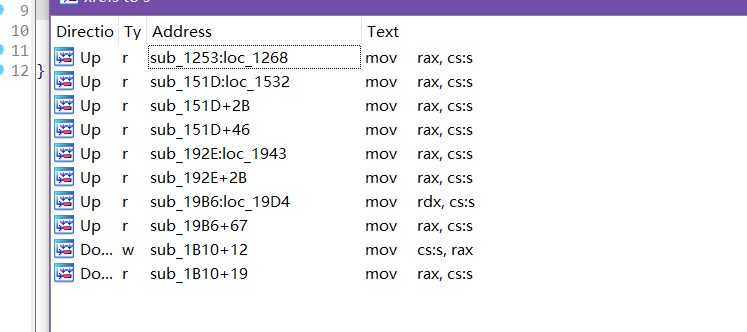
从下往上执行
Likemayasp
这题看起来是个ASP壳,但是PE识别的结果是UPX壳
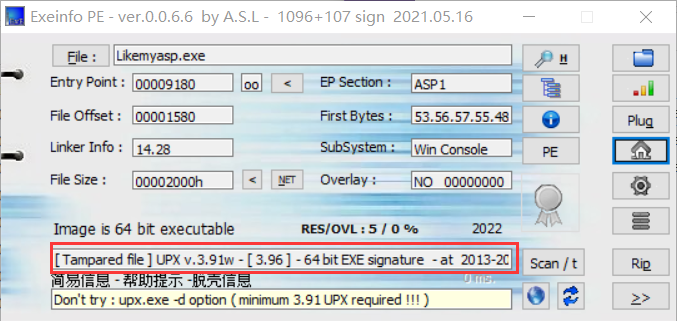
可以利用010修改壳头即可用UPX工具破开。当然也可以利用程序在运行的时候自己解壳的特性来动态调试。
ida打开,选择Local Windows debugger
Debugger——Attach to Process——选择需要调试的进程
动态调试即可到达加密函数
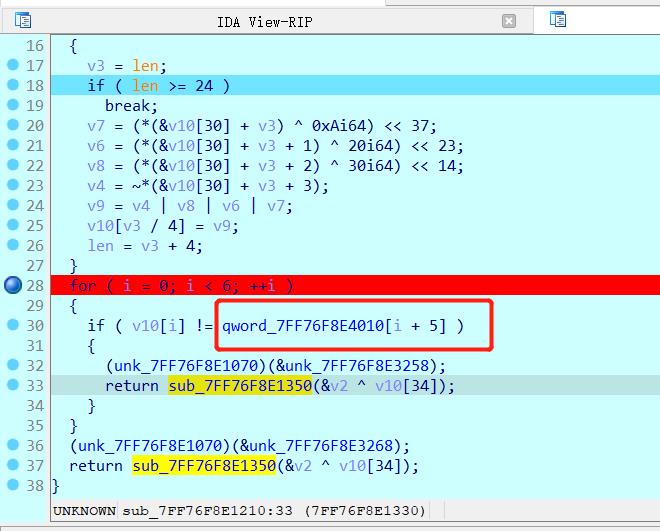
对密文进行一个长度判断后,位移后4个数一组进行判断
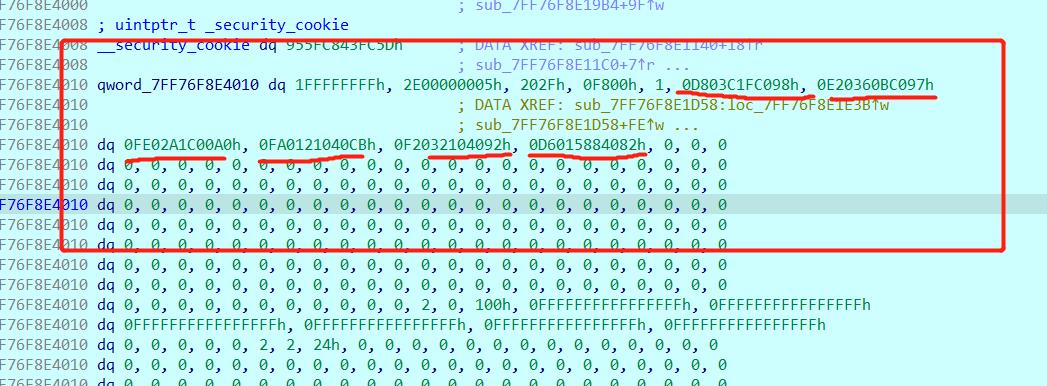
写py脚本解密
1 | x = [0x0D803C1FC098, 0x0E20360BC097, 0x0FE02A1C00A0, 0x0FA0121040CB, 0x0F2032104092, 0x0D6015884082] |
1 | flag{x1hu@n_w0_4sp_ma??} |
Petals
ida64打开
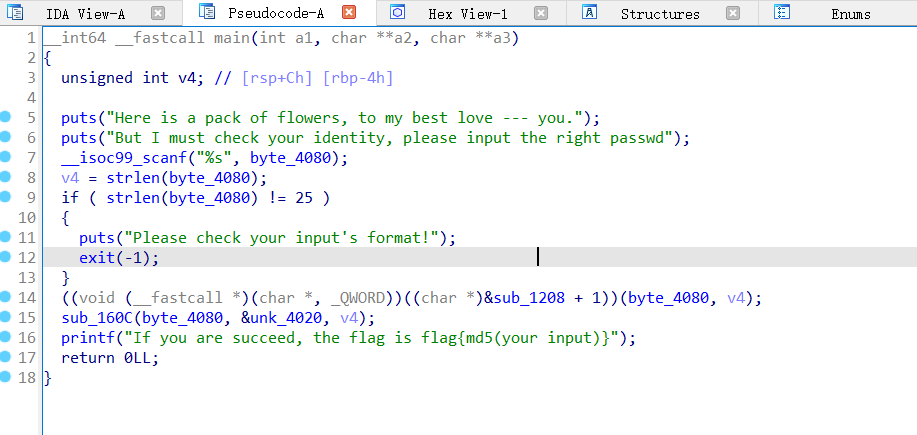
sub_160C是判断函数
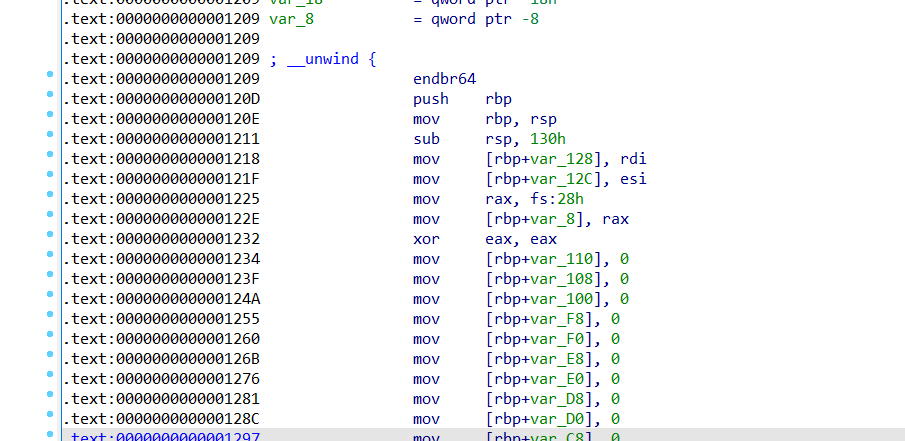
sub_1208 + 1无法跳转到函数,查看汇编
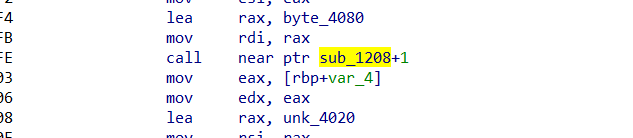
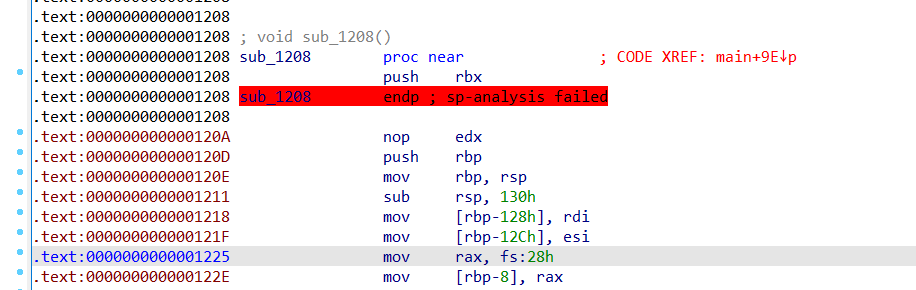
发现花指令,上面多了一行push rbx
D 变为数据后重新定位
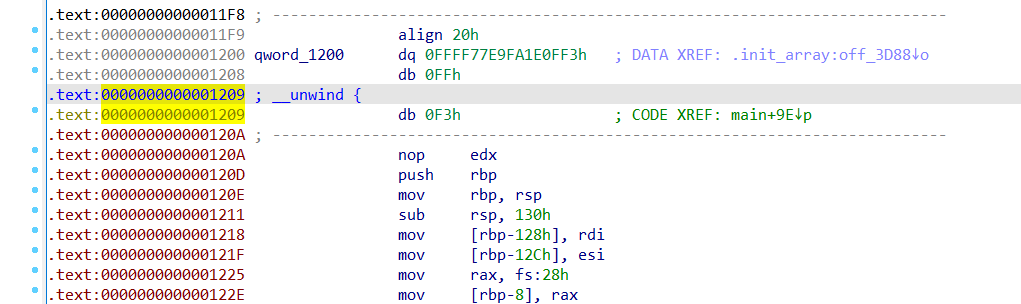
不难看出09才是函数的开头
选中后按p定义为函数
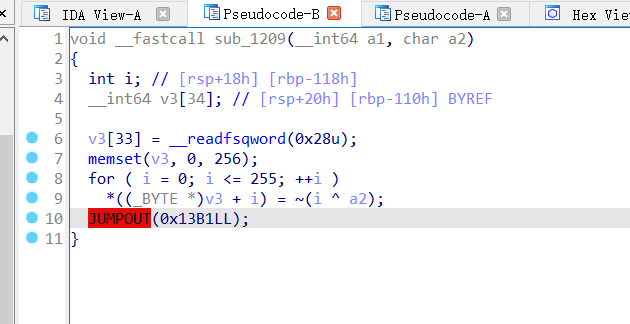
然而修改后还有红色的,打开汇编再往下看
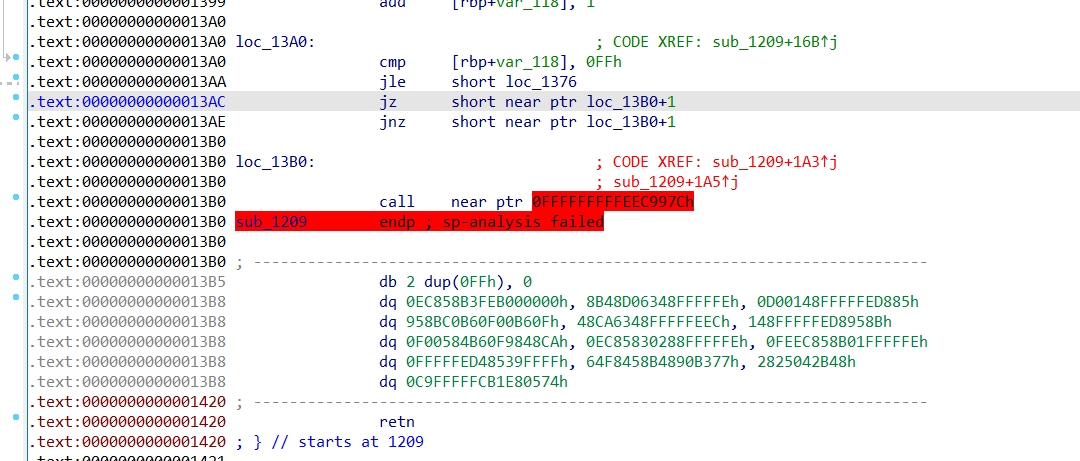
jn jnz 花指令
D 完后 nop掉多余的垃圾数据
一定要nop掉,这两节本来应该是同一个函数,被垃圾数据分割后不仅反汇编错误,还错误的将sub1208识别为void,原本应该是有返回值的。不nop掉会导致前半部分的函数不完整而且使得后半部分的函数的变量无法正常继承。
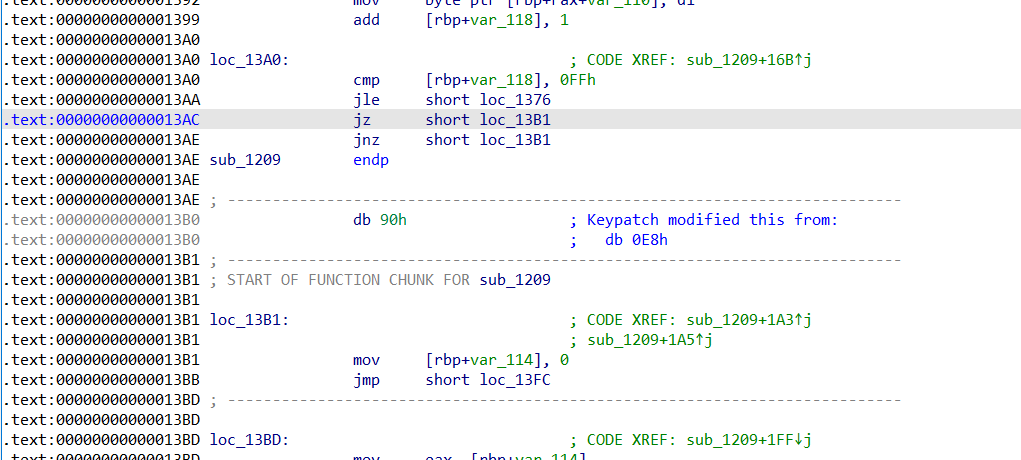
并且将函数的返回值定义为int *
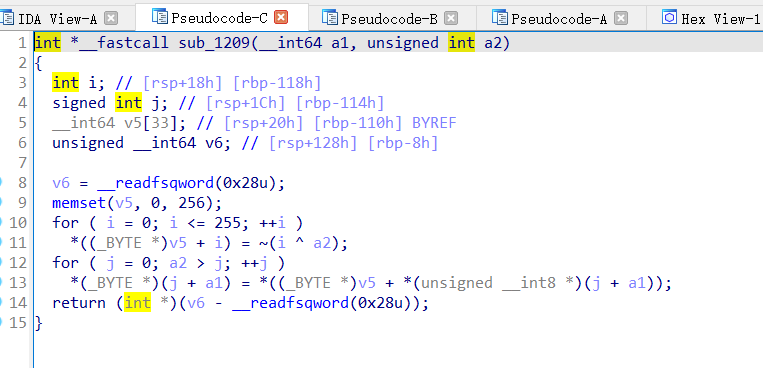
首先初始化一个v5的数组作为码表,然后再进行替换,逆向的方法选择爆破
1 | import hashlib |
1 | flag{d780c9b2d2aa9d40010a753bc15770de} |
Week 3
Zzzzz3333
32位IDA
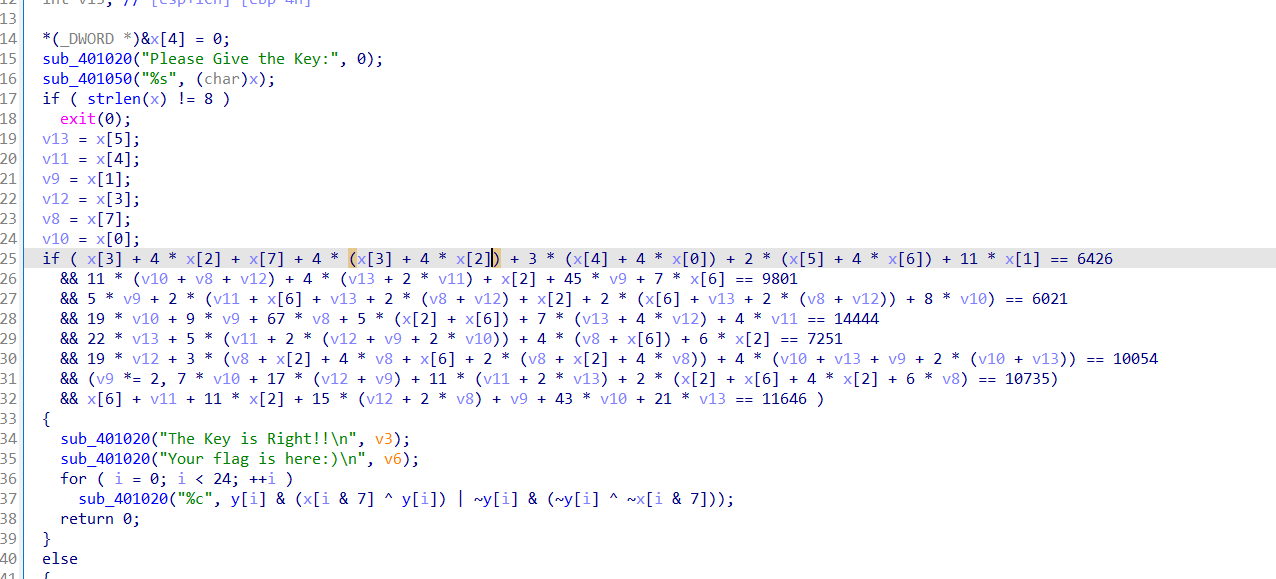
用z3解出x,然后再输出
1 | from z3 import * |
flag{Zzzz333_Is_Cool!!!}
EzTea
64位ida
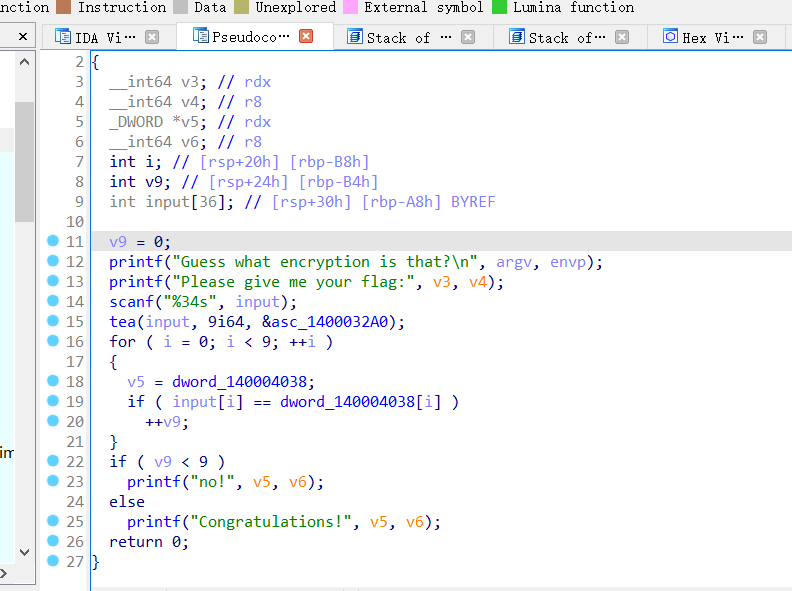
点开函数,发现是xxtea加密
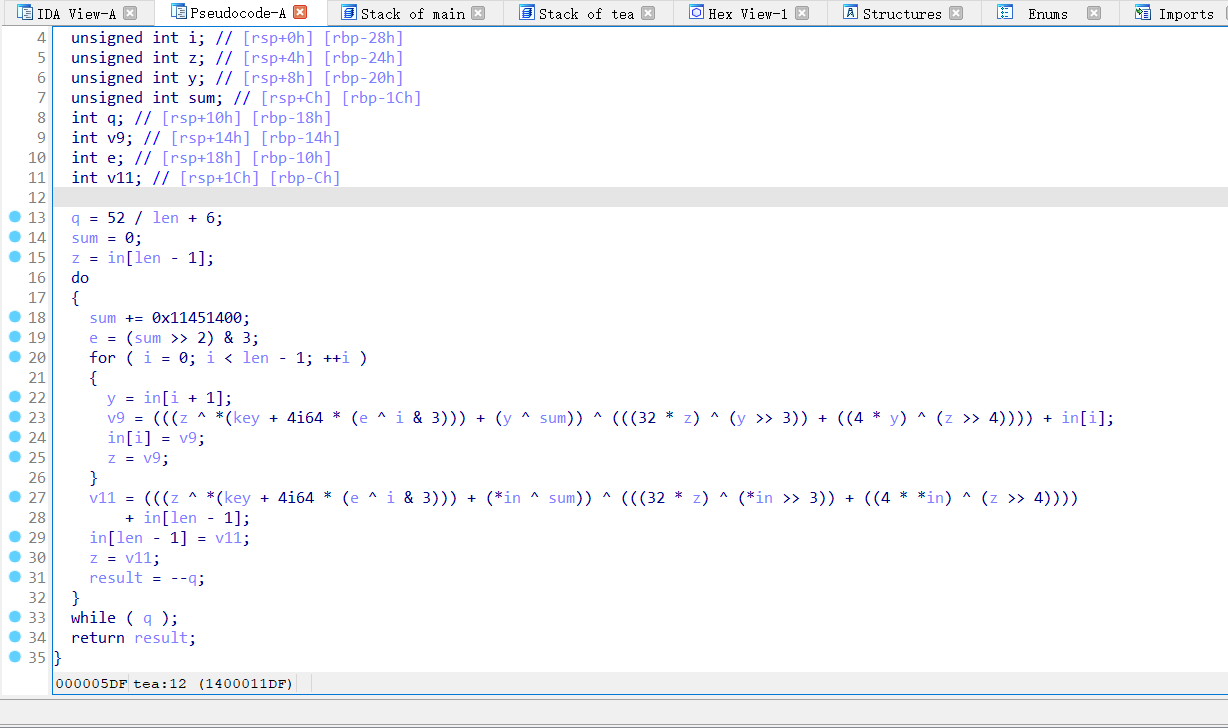
只不过修改了MX和magic值
脚本
1 |
|
1 | flag{H0P3_U_L1k3_Th15_CUP_0f_TEa.} |
The Slider’s Labyrinth
32位ida
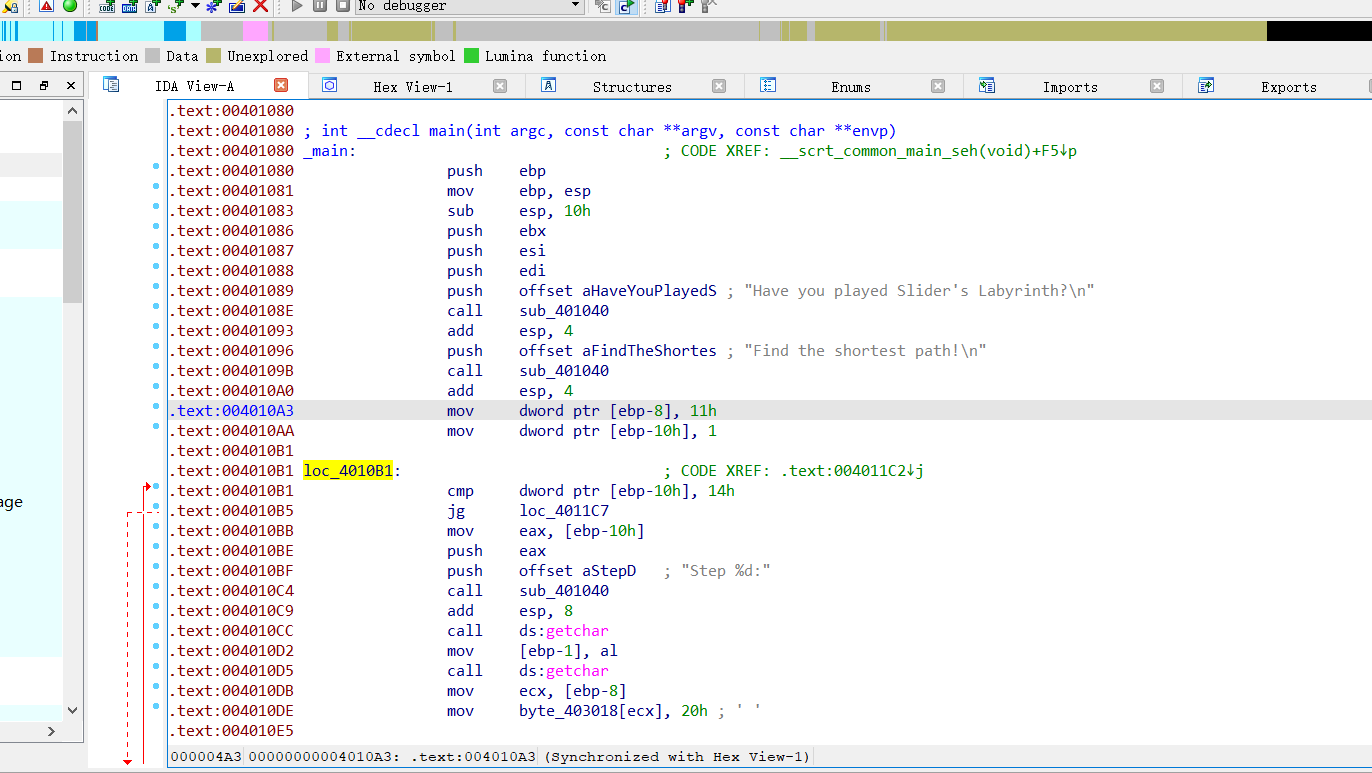
这里加了好几个花指令
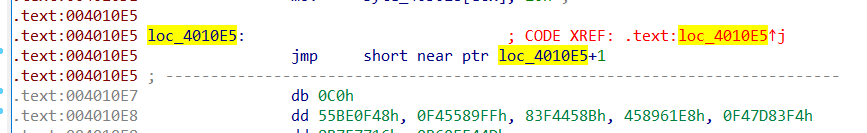
主要都是这种死循环的,直接nop
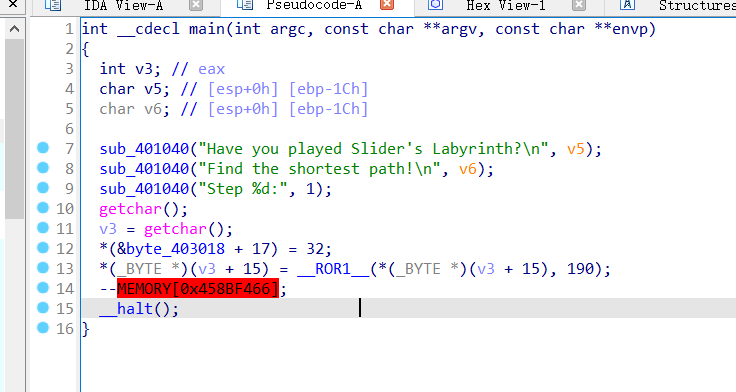
还是红的,再将hlt给nop掉
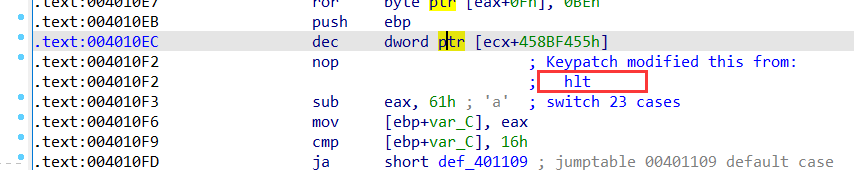
于是就能正常显示了
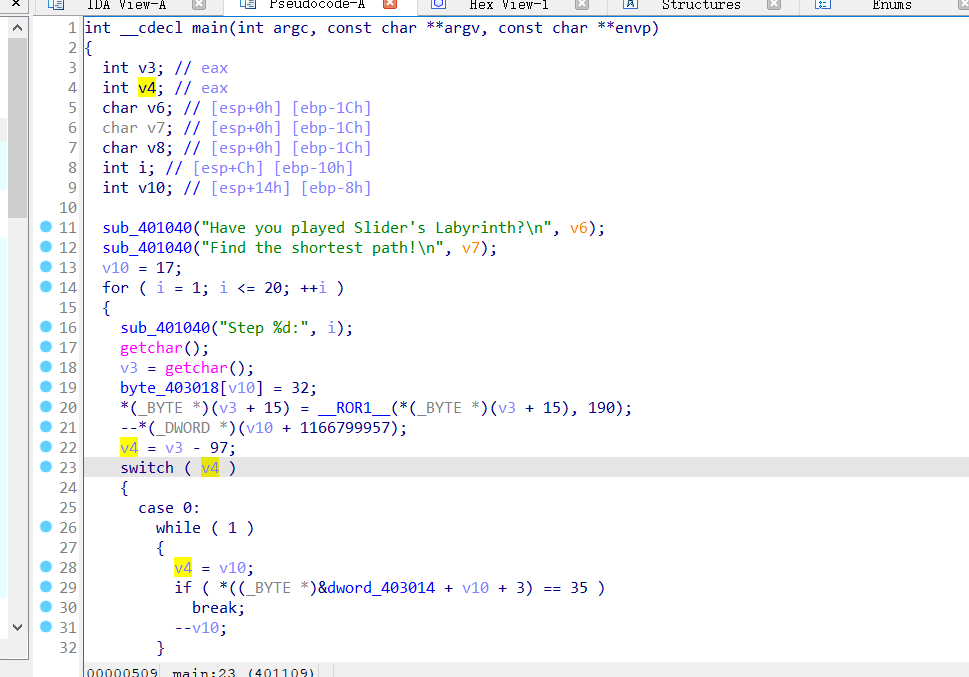
分析过程
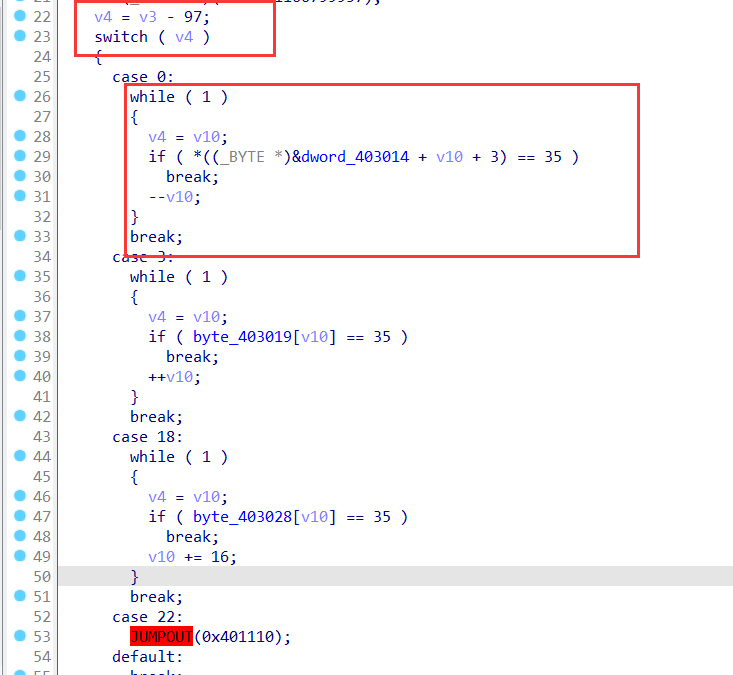
发现将输入减掉97后四个case,即w a s d控制上下左右,while循环让人物一直走到墙才停止,并且每行的长度是16
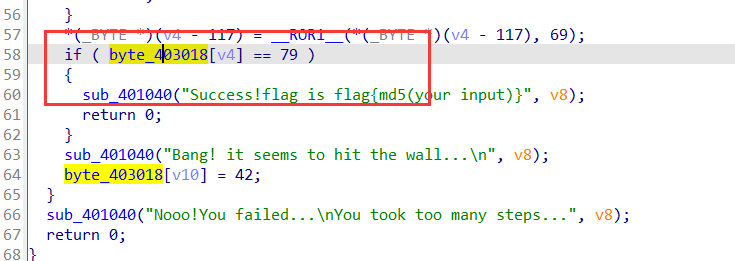
找到地图
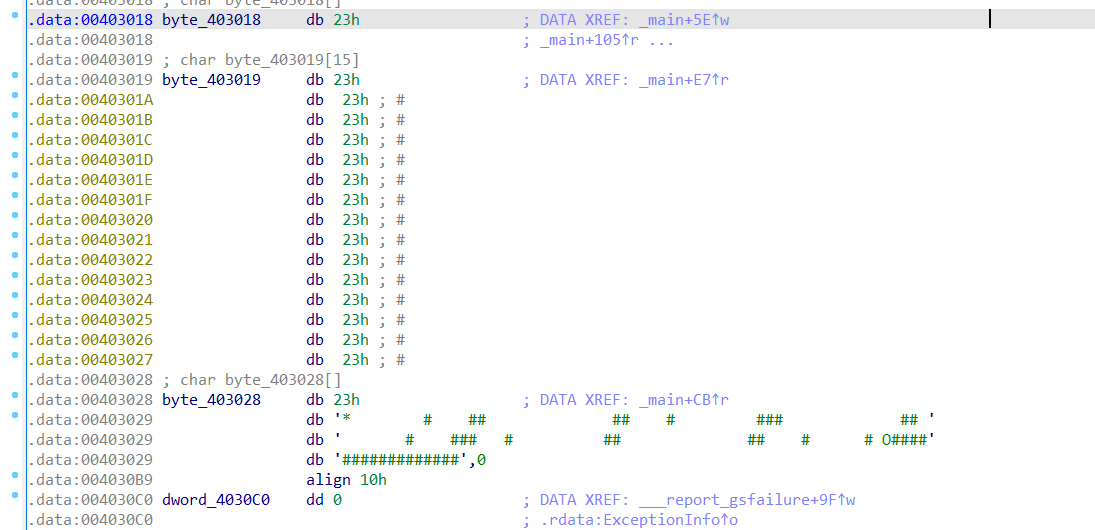
大概就长这样
| # | # | # | # | # | # | # | # | # | # | # | # | # | # | # | # |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| # | * | # | # | ||||||||||||
| # | # | ||||||||||||||
| # | # | # | |||||||||||||
| # | # | # | |||||||||||||
| # | # | # | # | ||||||||||||
| # | # | # | |||||||||||||
| # | # | ||||||||||||||
| # | # | # | O | # | |||||||||||
| # | # | # | # | # | # | # | # | # | # | # | # | # | # | # | # |
走法不唯一,题目要求的是最短的一条
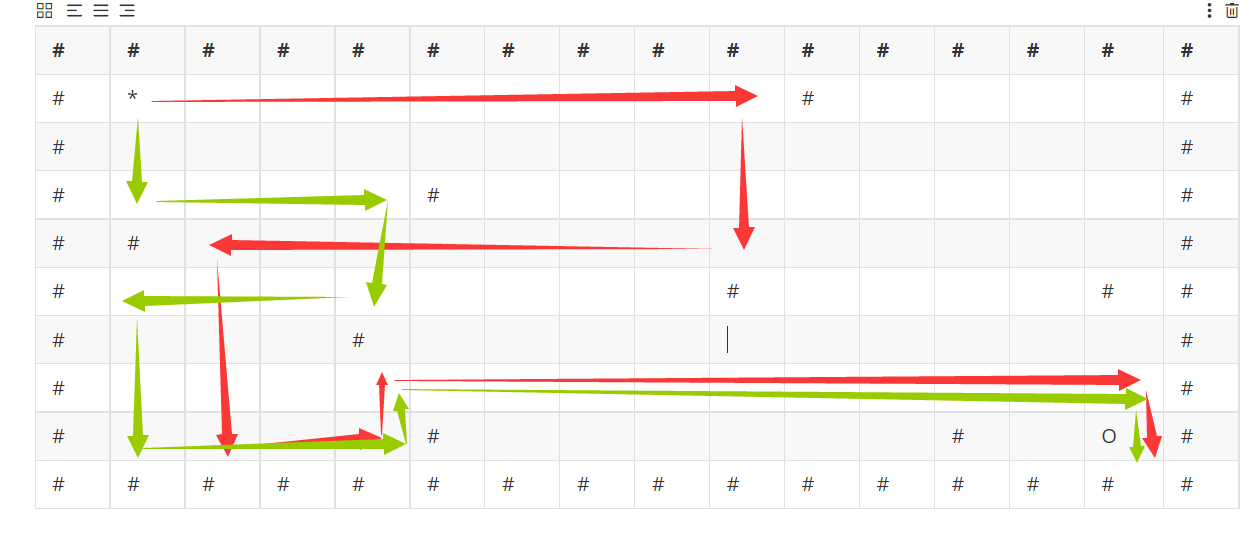
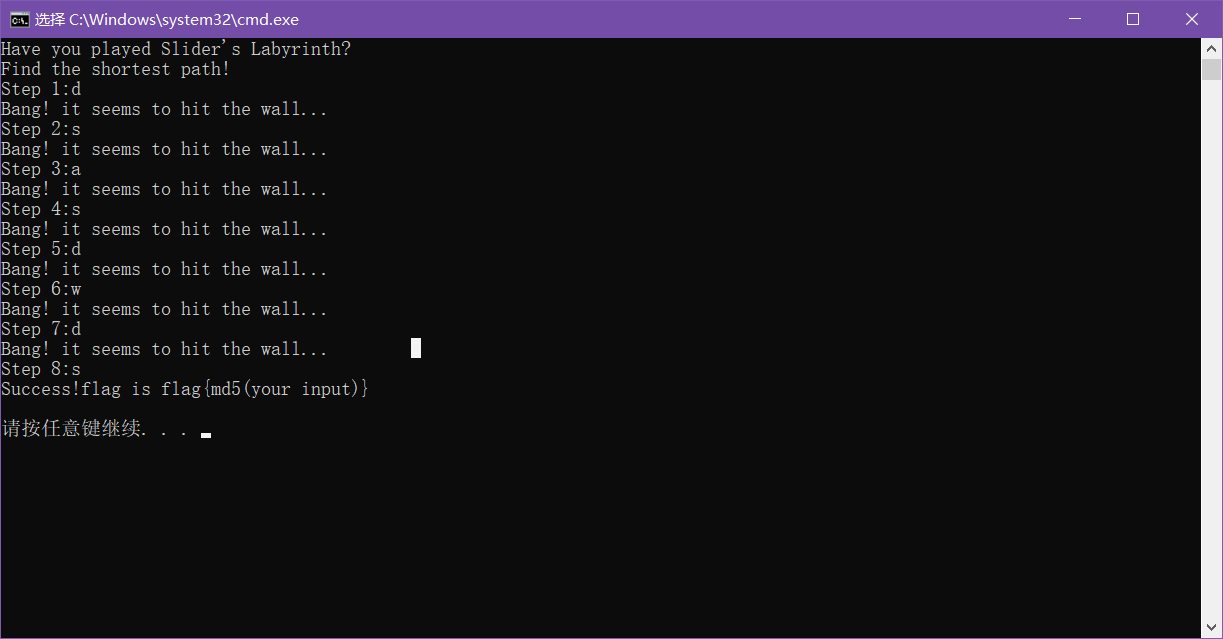
1 | flag{f71516bdf07abd7bc0668db9d6352364} |
Annnnnnggrr
本题主要考察angr的使用
ida无壳
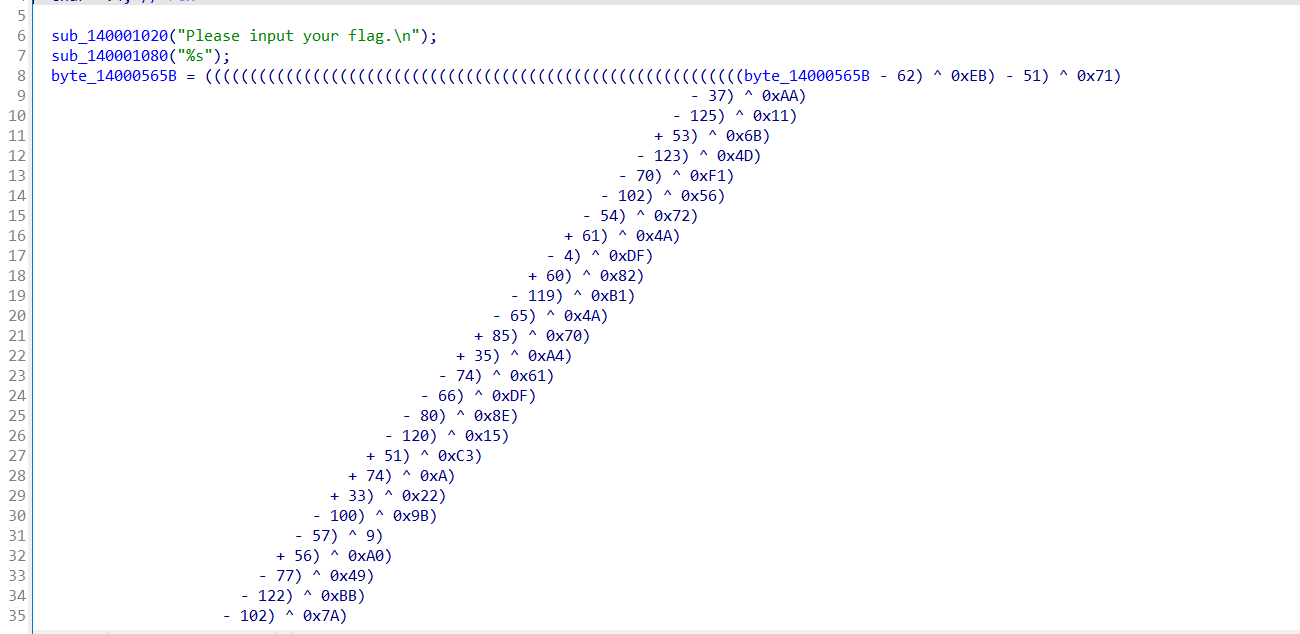
大哥爬楼梯
没什么好说的,基本上就是对着angr的模板写就行
1 | import angr |
1 | flag{umm_I_can't_calc_1t_@t_all} |
funnyOTL_1
ida64位
这题主要是对c++的库函数的熟悉度
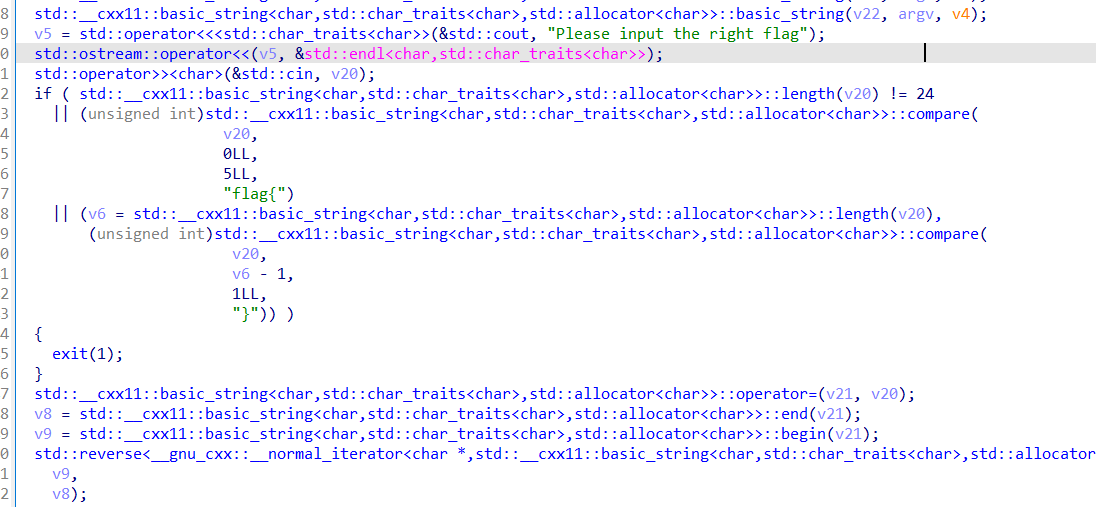
输入flag{}包裹的总长为24位的密码
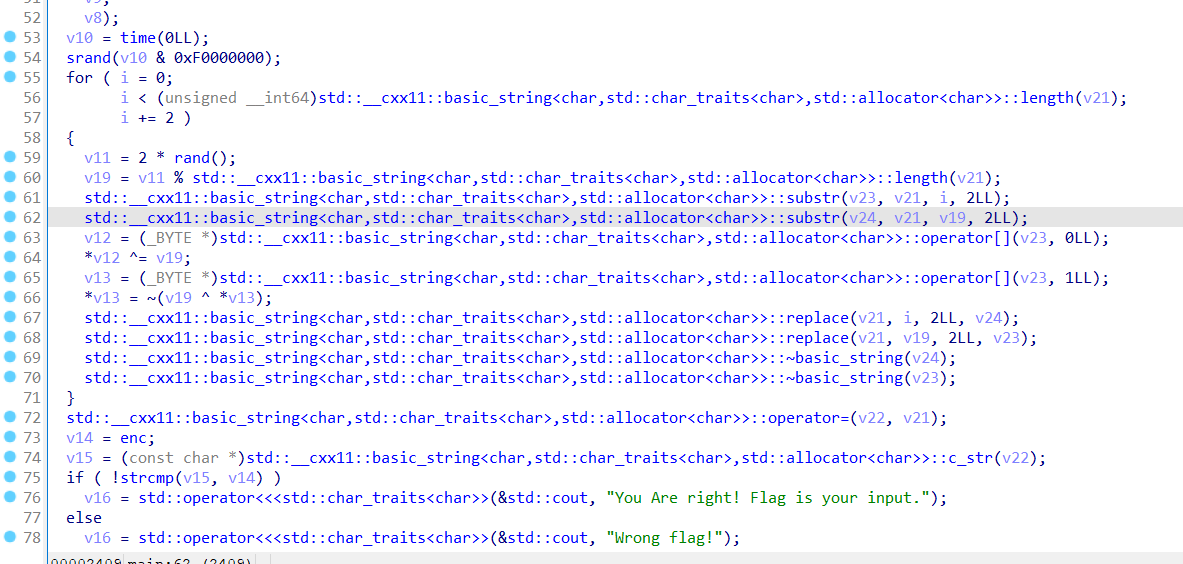
然后就是加密后交换,唯一问题是这个随机数的问题,经过测试,Linux环境下随机数的值和Windows下是不一样的,以后要注意系统之间的差异
写脚本
1 | enc =[ 76, 171, 120, 73, 104, 157, 81, 121, 117, 95, |
1 | flag{OTL_n0w_u_know_STL} |
Week4
Hash
1 | import hashlib |
1 | flag{Easy_Hash_And_Y0u_Solve_1t_Quickly!!} |
Exception
32位ida
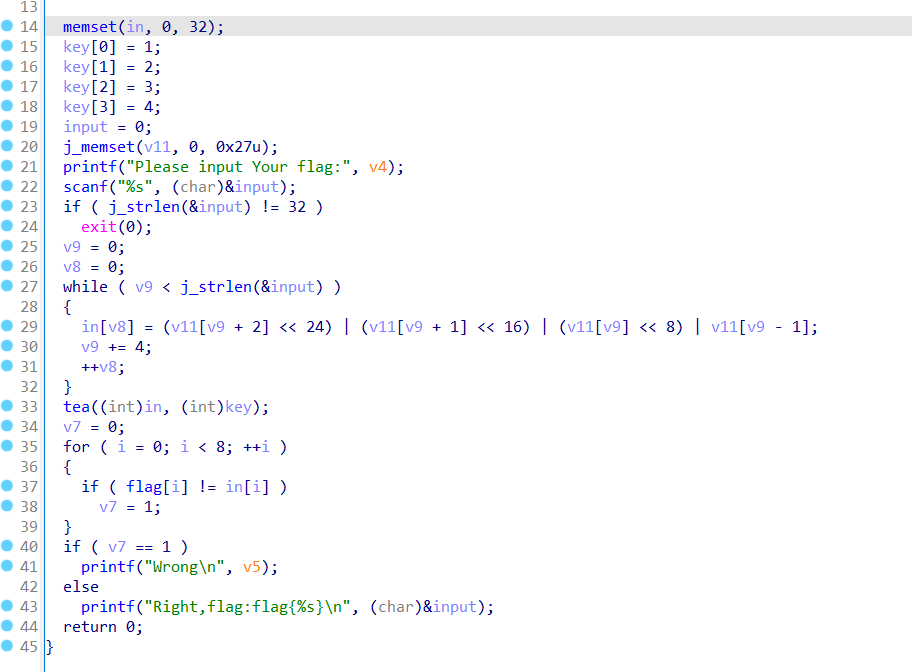
乍一看只是单纯的tea,但是直接逆是解不出来的
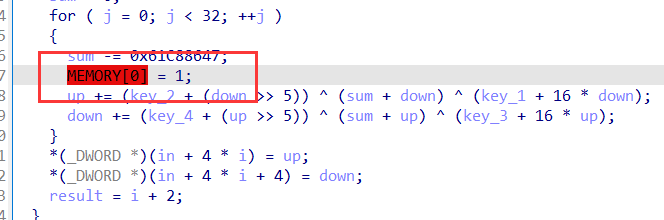
在tea加密里面塞入了一个try块
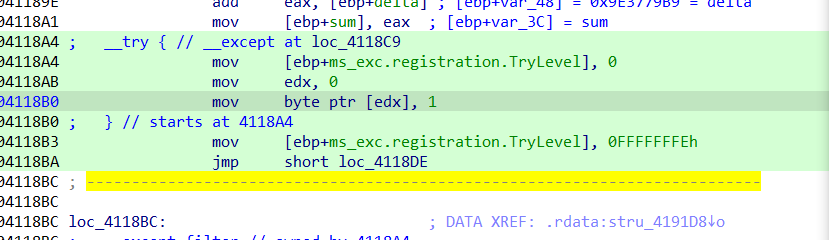
分析异常,发现异常过滤器的返回值恒为1,即一定进入异常处理
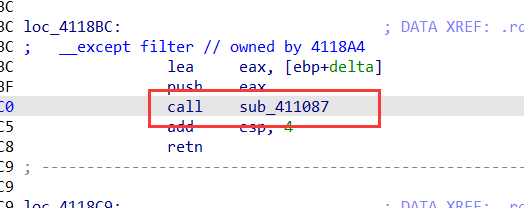
于是直接分析异常处理
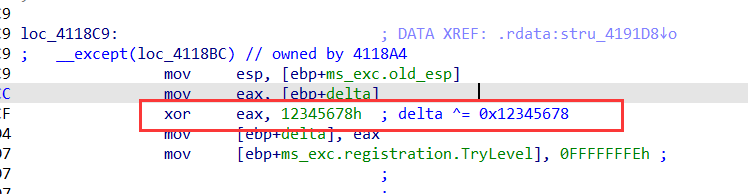
这里将delta 异或了一个0x12345678,编写脚本
1 |
|
1 | flag{44C3A7F112DA2BE728F451C5E2D09558} |
HelpMe
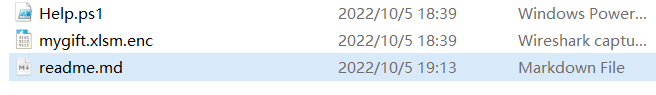
解压后发现有一个ps1的owershell的脚本文件
题目的意思是一个excel文件被加密了
.enc是一个二进制文件,突破点在于Help.ps1脚本
1 | $mypath = Split-Path -Parent $MyInvocation.MyCommand.Definition |
真正的脚本应该是那段base64数据,python解密后再用gzip解压(这个是看网上那些恶意代码分析的文章看来了)
1 | import base64 |
跑完就会出现真正的脚本
1 | $timestamp = ([DateTimeOffset](Get-Date "Sat Oct 01 2022 20:22:21")).ToUnixTimeSeconds() |
首先用Sat Oct 01 2022 20:22:21生成16位随机数,然后再AES的ECB模式加密文件
首先写脚本,用powershell跑出key
1 | $timestamp = ([DateTimeOffset](Get-Date "Sat Oct 01 2022 20:22:21")).ToUnixTimeSeconds() |
1 | key = [105, 192, 50, 118, 175, 152, 128, 155, 147, 80, 183, 37, 190, 22, 242, 78] |
然后AES对mygift.xlsm.gift文件进行解密
1 | from Crypto.Cipher import AES |
然后就会生成一个ans.xls文件。题目说是excel工作表就直接加.xls上去了
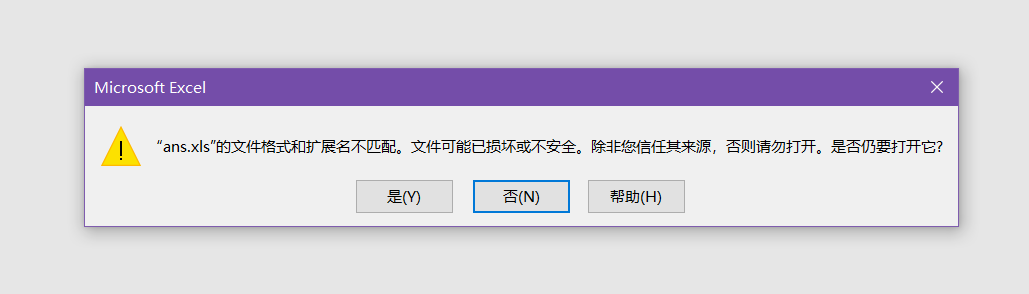
但是文件损坏了,用在线xls修复工具修复后再打开
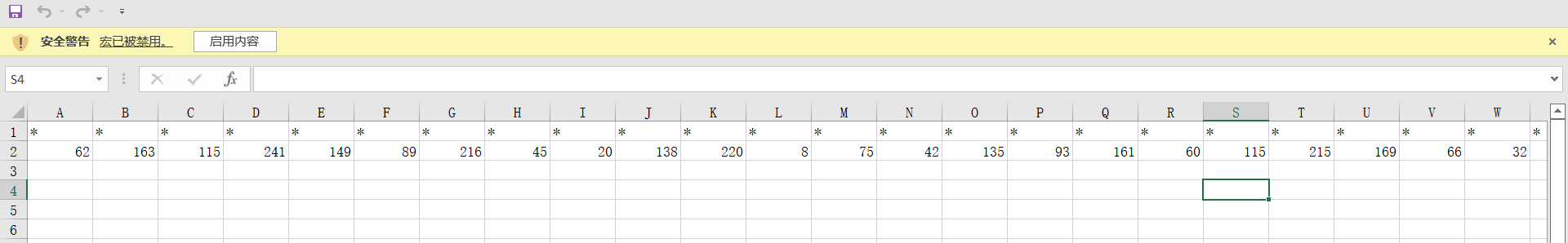
出现一个数组并且有个宏,猜测有可能是宏里面写了什么东西,Alt + F11打开vba编辑器,发现加密的代码
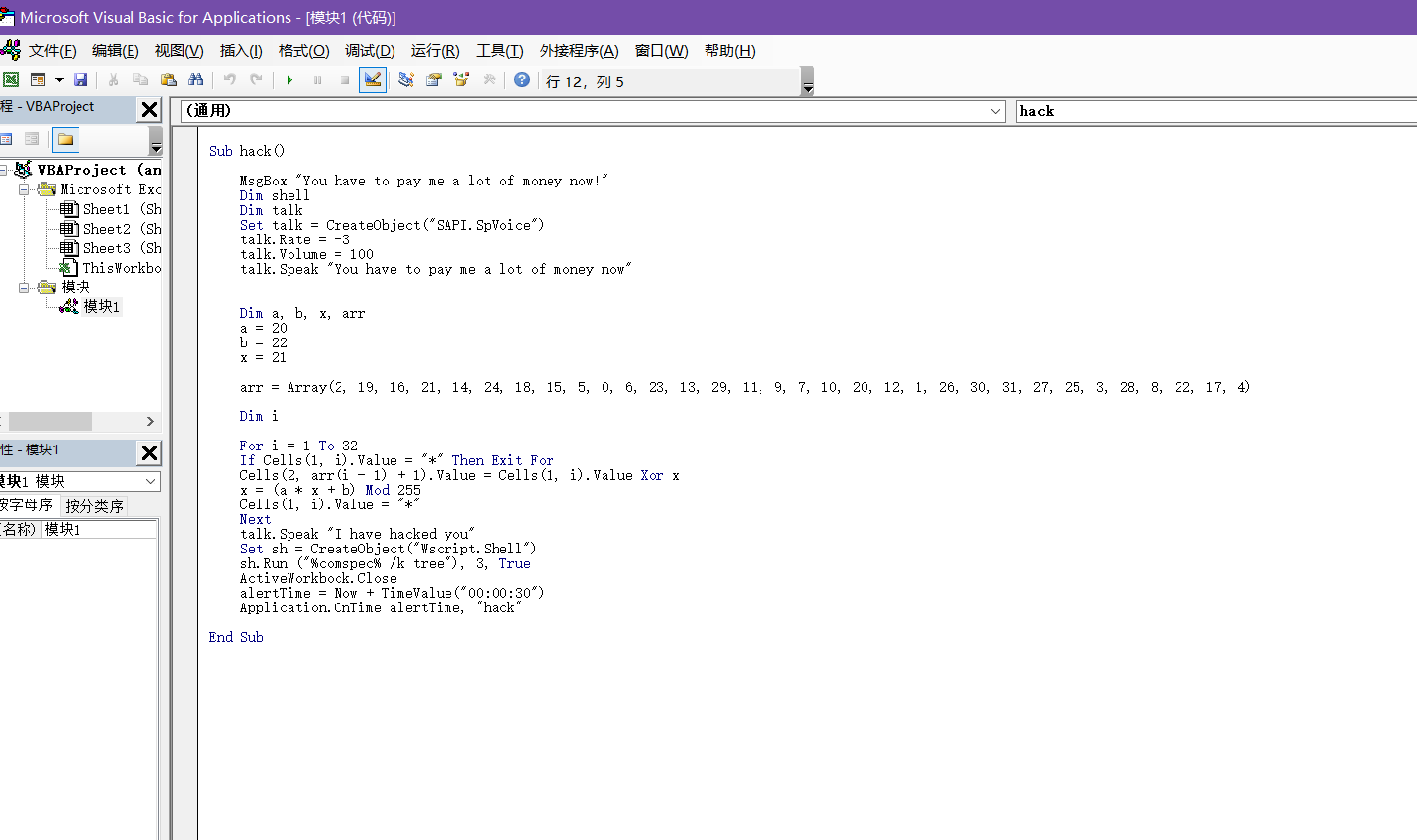
大意是将excel里面是数组按照arr数组里面的顺序和x异或,然后x = (a * x + b) % 255,脚本解密
1 | enc = [ 62, 163, 115, 241, 149, 89, 216, 45, |
1 | flag{This_is_@_begin_about@hack} |
Week5
拔丝溜肆
64位ida无壳
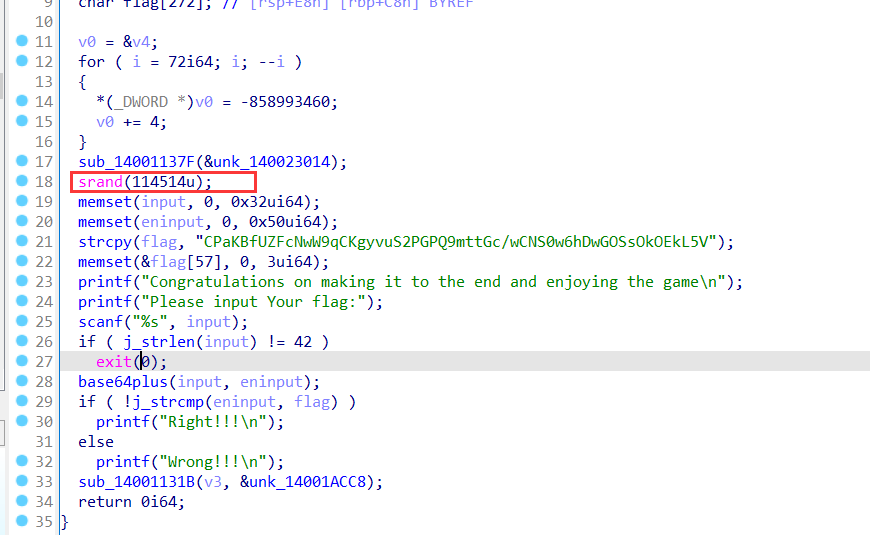
记住这个srand(114514)
点进base64plus函数
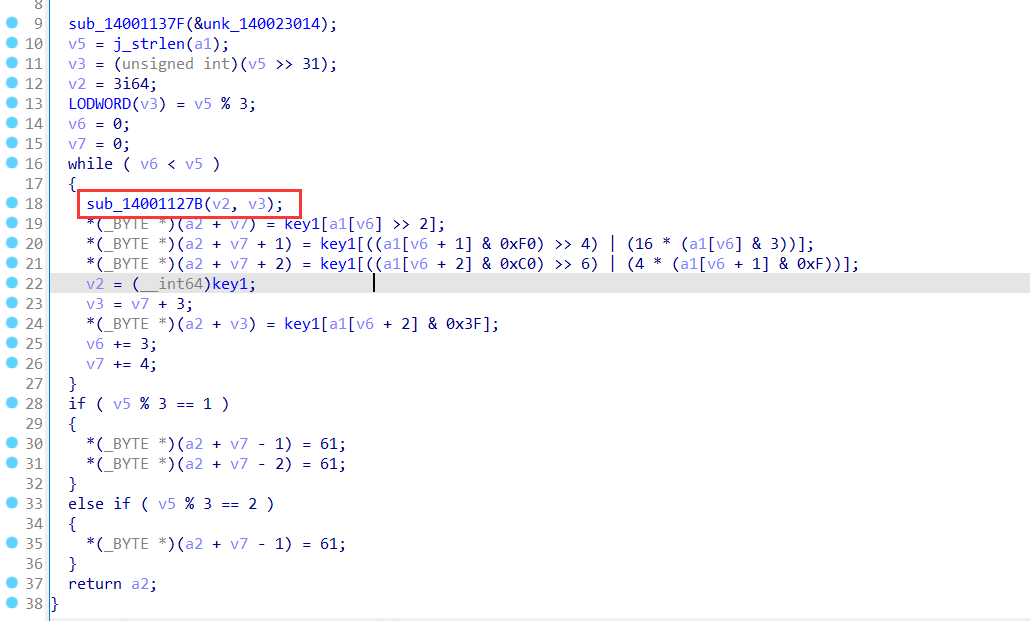
发现在基本的base64上还多了个函数
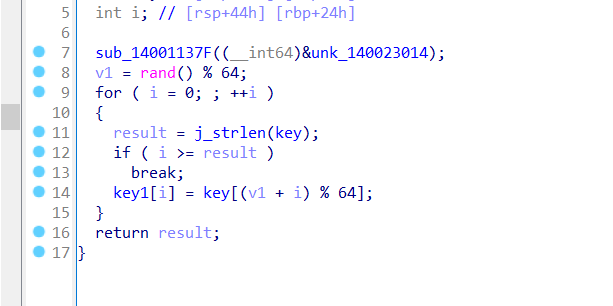
这里每次循环都生成一个随机数然后让key,即码表整体向右循环位移
随机数种子则是之前出现过的114514
写脚本得出随机数
1 | int main() |
然后只要在base64解码的时候加入码表移动就好了
当然也可以解码14次只取对应位置的三个字符
flag{12573882-1CF1-EB5E-C965-035B1F263C38}
E4sy_Mix
ida32位无壳
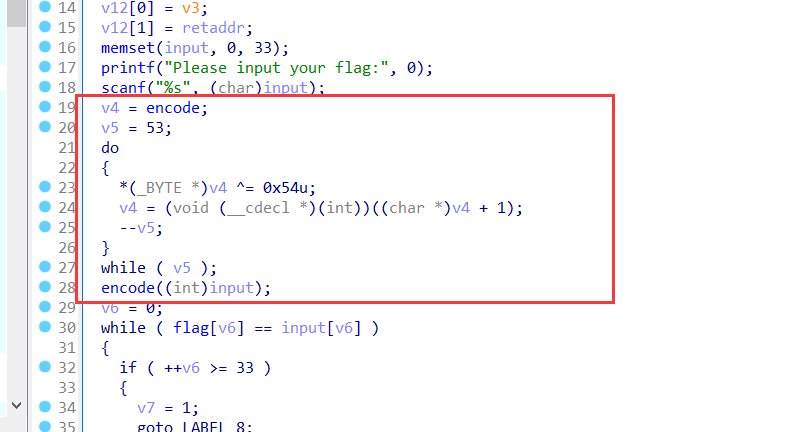
SMC自修改,使用idc脚本
1 |
|
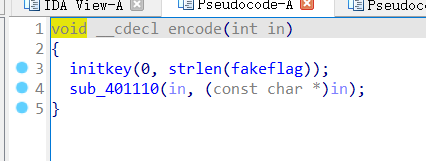
分析之后发现第一个函数只是单纯的初始化一个key数组
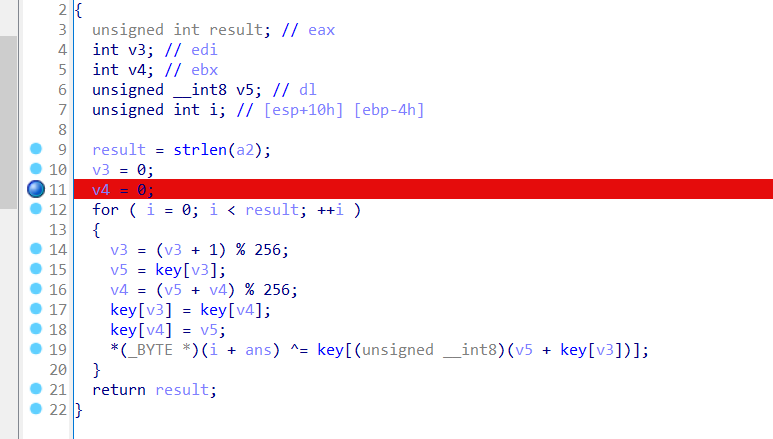
下断点动调后对着抄跑一边就行了
1 | flag = [ |
1 | flag{RC4_and_SMC_is_interesting!} |
Petals Level Up
这道题的关键在于花指令
64位无壳
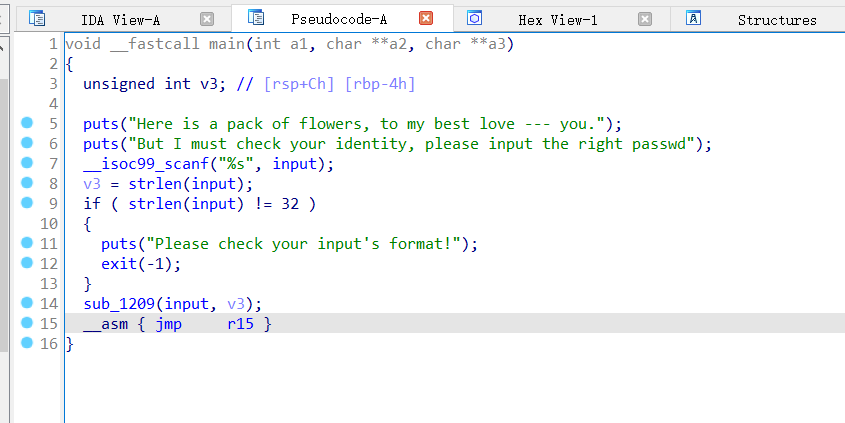
很明显有花指令
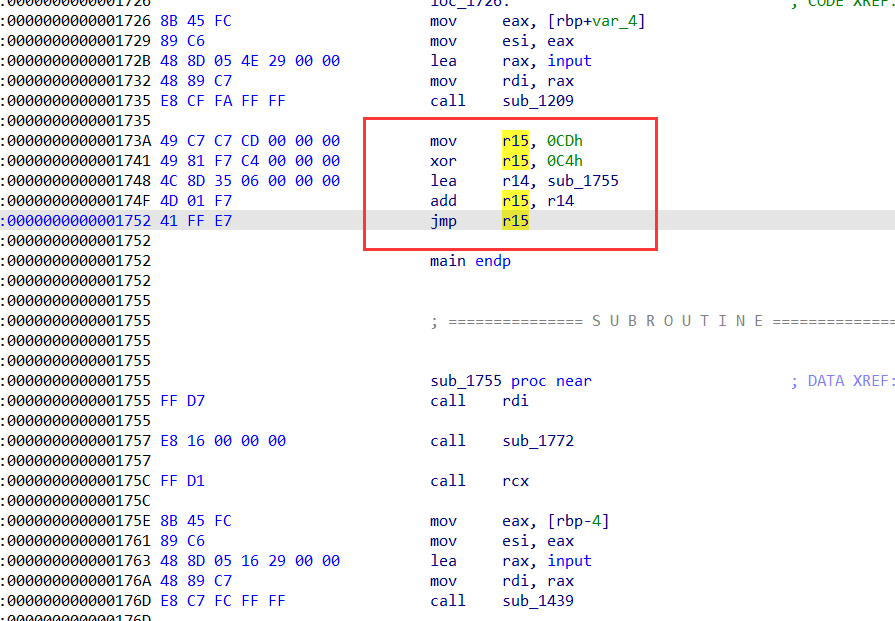
很明显,最后跳转的地址等于0x1755 + (0xcd ^ 0xc4) = 0x175e
然后将0x173a 到 0x175c这段给nop掉
类似的还有几个
最后应该是
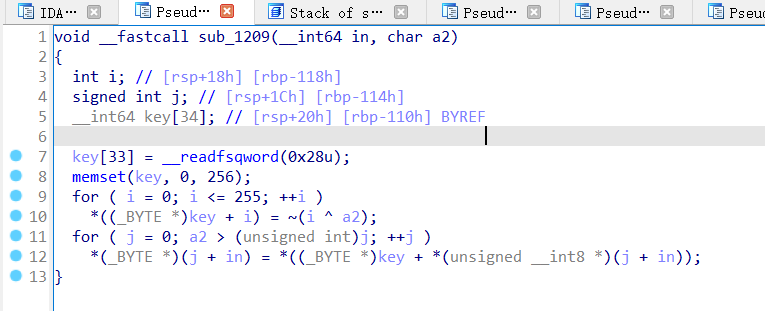
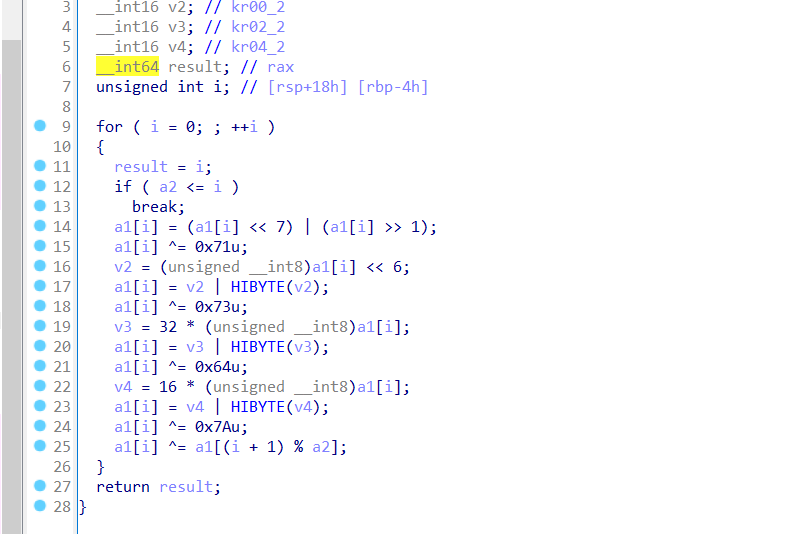
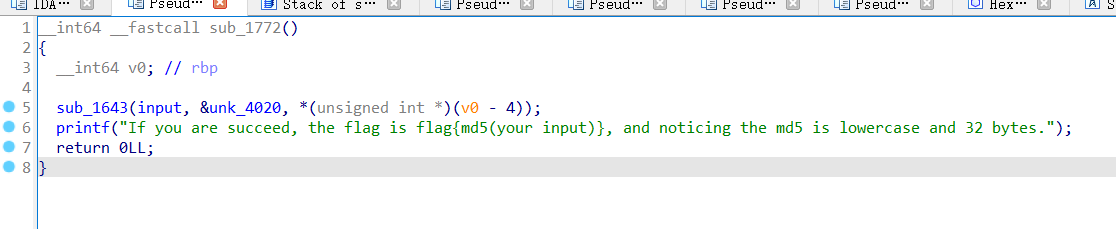
写出脚本
1 | import hashlib |
1 | flag{d5658c0b4c44d4672d76b563a8505a66} |
babycode
.ll 文件是llvm下的字节码的文本形式
于是我们需要将其转换为可执行文件来进行分析
将字节码变为汇编后就能用clang编译
1 | llvm-as task.ll |
1 | clang task.bc -o struct |
然后拖进ida进行分析
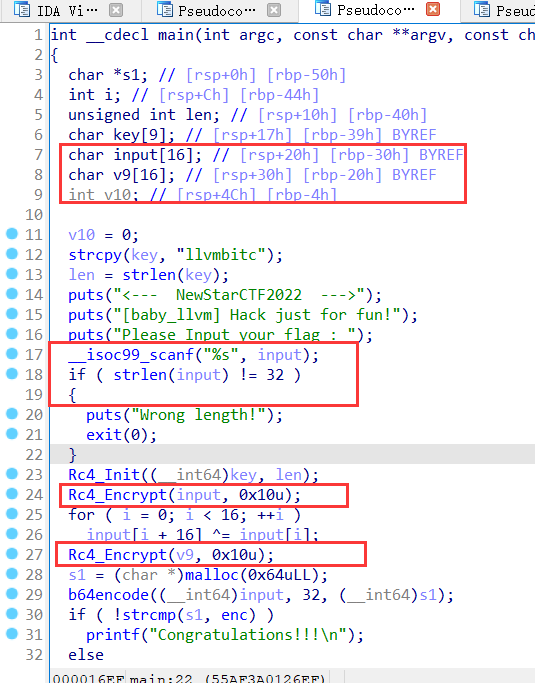
不难但是有几个点是要留意的
这里输入靠溢出分成了两节,先rc4加密前半节,然后将后16位和前16位异或后再用同一个s盒rc4加密,再整体base64
rc4是标准的,key = llvmbitc
base64坑有点多
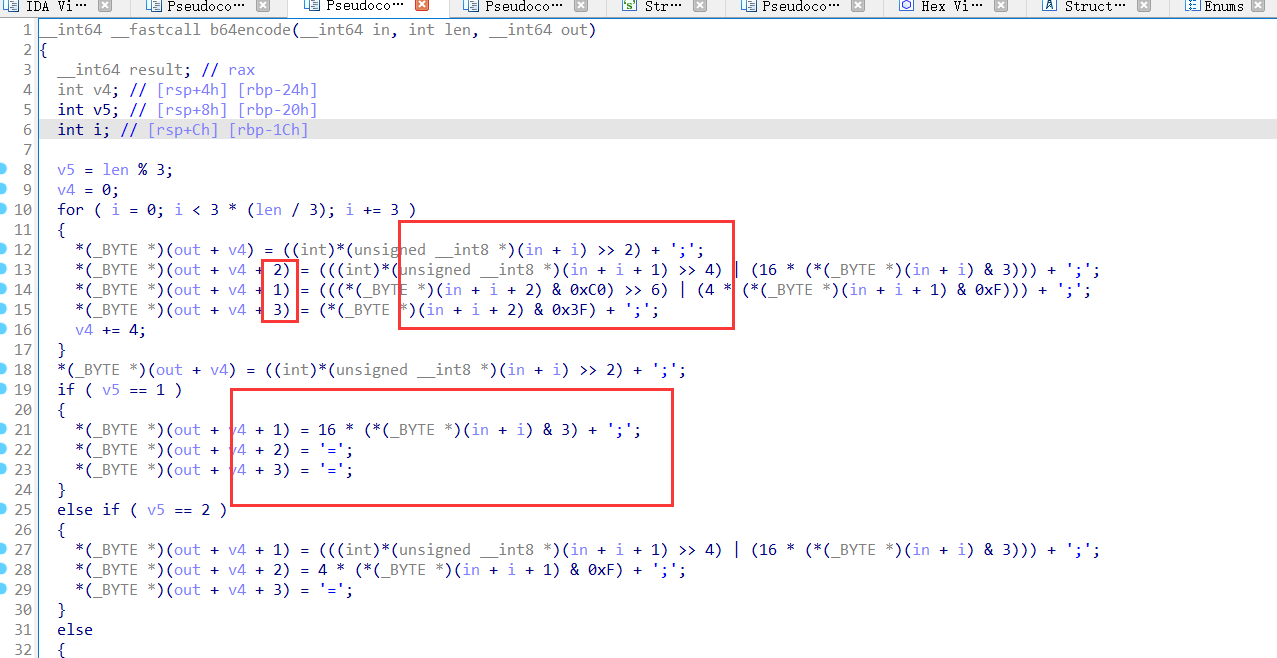
一个是他3转4是时候顺序不太一样,但是结尾的3转4顺序是正常的
码表则是以;开头的64位
写脚本
1 | s = [0] * 256 |
1 | flag{Hacking_for_fun@reverser$!} |