520迎新赛wp
2022dest0g3(RE)
Day1
simpleXOR
64位无壳,丢进ida
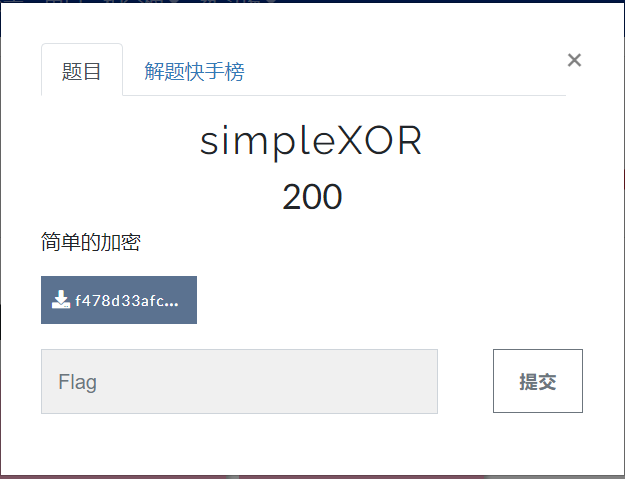
将input[i]与i相加再与247异或,然后和ans比较出flag
1 | int main() |
解出Dest0g3{0bcgf-AdMy892-KobPW-hB6LTqG}
hi
64位无壳,ida
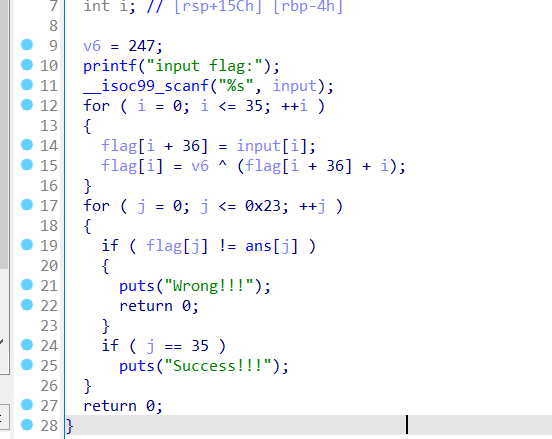
首先对enc进行拆解
1 | int main() |
得出enc数组后开始爆破
1 | int main() |
得出Dest0g3{f982cd79-d7a3-0874-aa0b-a5b37e4445c8}
Day2
tttea
32位ida, 无壳
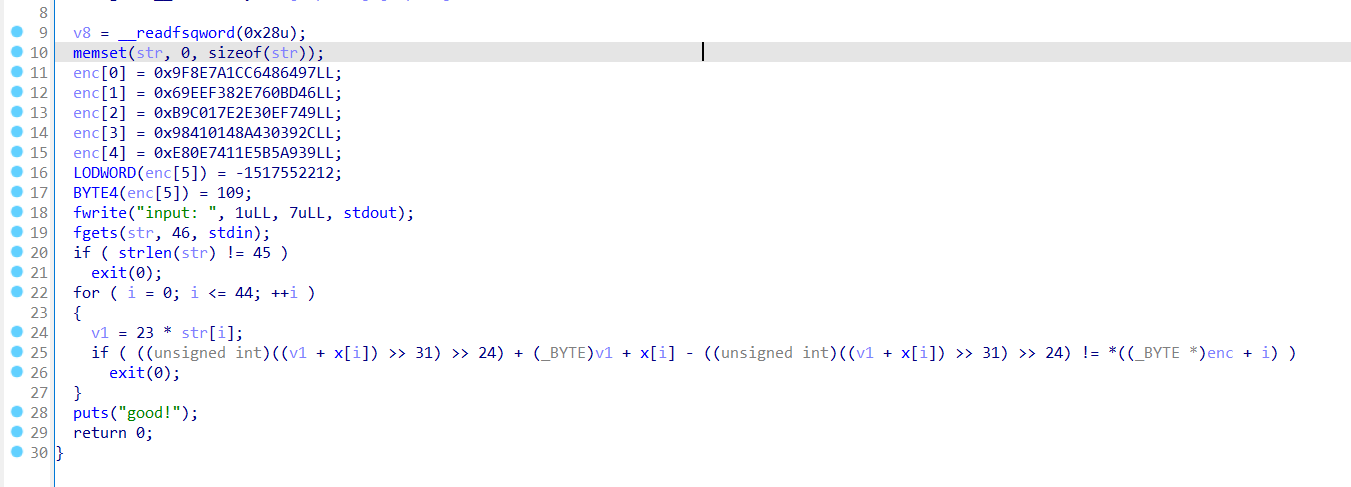
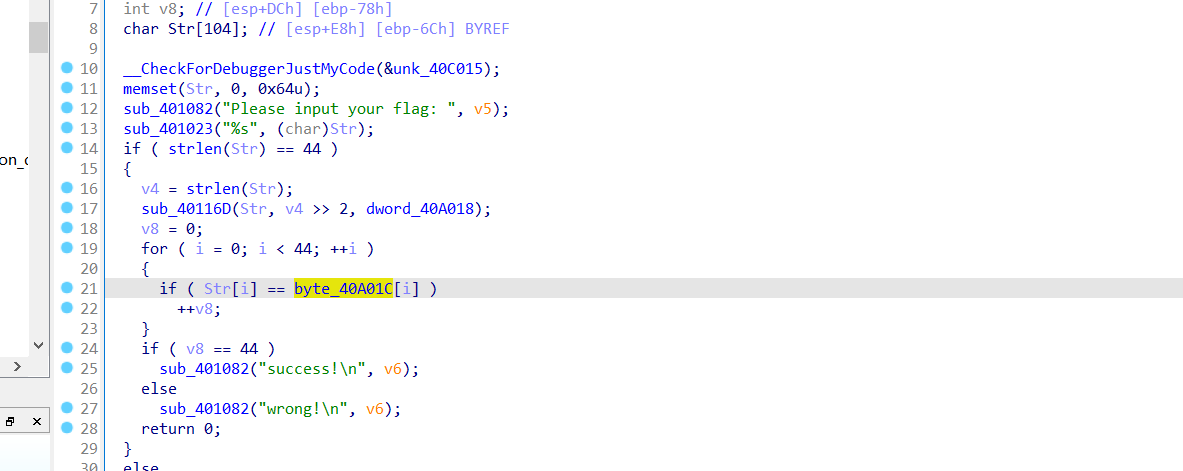
输入为str,经过函数sub_40116D后与byte_40A01做比较
进入sub_40116D,发现这是个xxtea加密,v4 >> 2代表着组元为4, 即将44位的数组分成11段,写脚本的时候需注意类型转换。
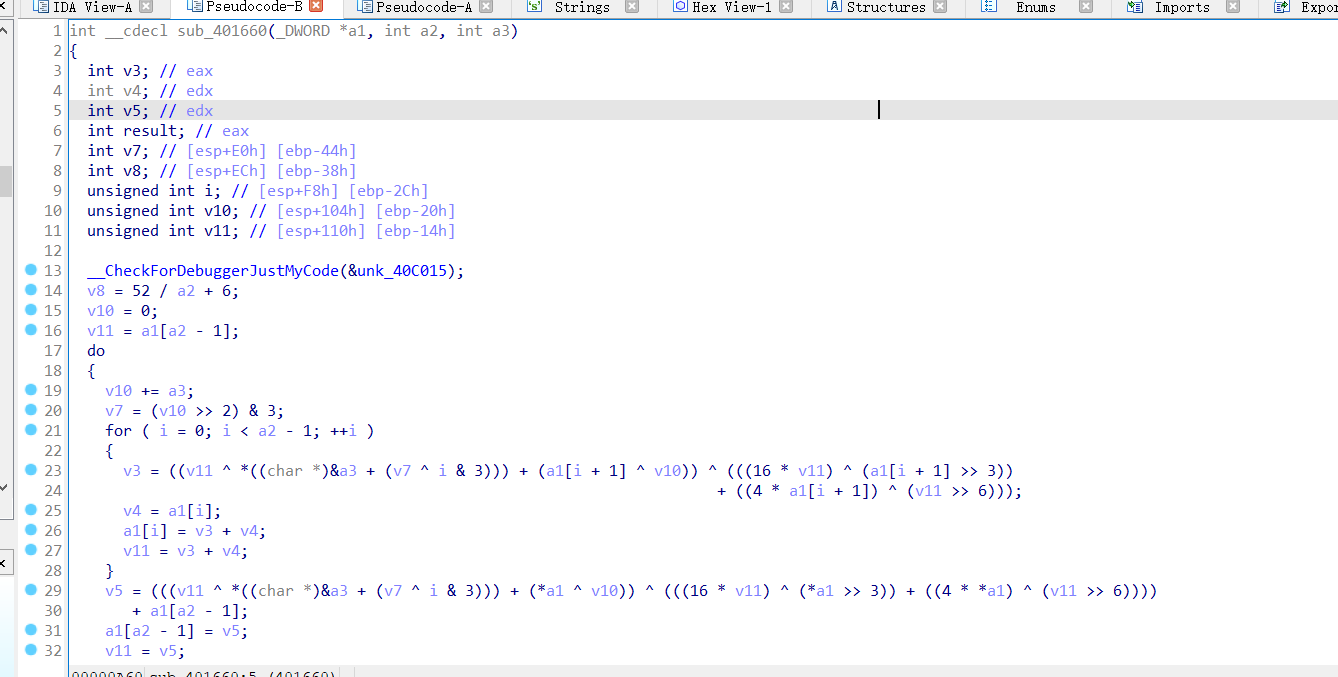
为xxtea加密,不过与原版修改了移位的值和delta
注意,有TLS反调试
因此对其进行分析
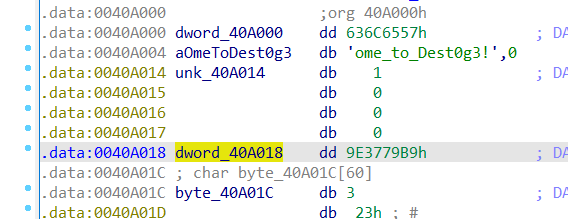
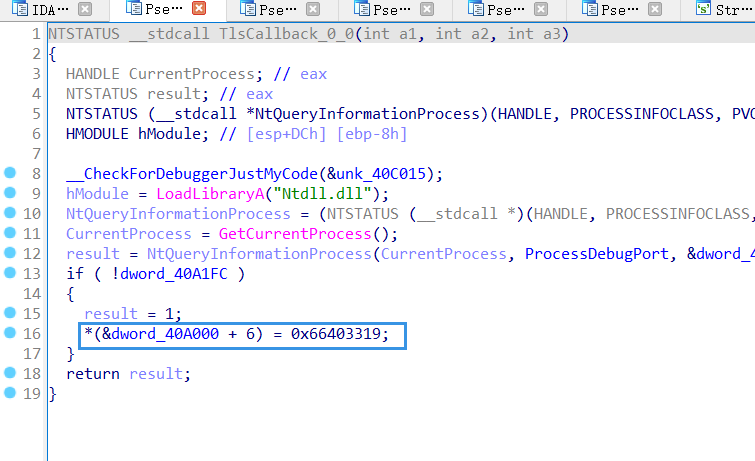
首先将0040A018的值改为0x66403319
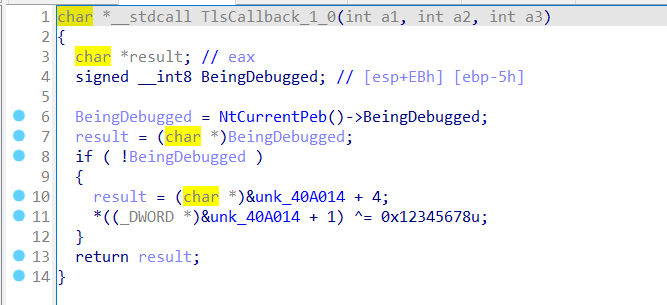
然后再与上0x12345678
即真正的delta为0x66403319 ^ 0x12345678,即0x74746561
1 |
|
得出flag:Dest0g3{73dd38c2-9d45-4f7a-9bd0-90a1e9907c1}